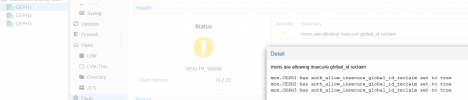
root@pxceph3:~# ceph mon metadata
[
{
"name": "pxceph",
"addrs": "[v2:10.10.20.20:3300/0,v1:10.10.20.20:6789/0]",
"arch": "x86_64",
"ceph_release": "nautilus",
"ceph_version": "ceph version 14.2.22 (877fa256043e4743620f4677e72dee5e738d1226) nautilus (stable)",
"ceph_version_short": "14.2.22",
"compression_algorithms": "none, snappy, zlib, zstd, lz4",
"cpu": "Intel(R) Xeon(R) CPU E5-1650 v4 @ 3.60GHz",
"device_ids": "",
"device_paths": "",
"devices": "",
"distro": "debian",
"distro_description": "Debian GNU/Linux 10 (buster)",
"distro_version": "10",
"hostname": "pxceph",
"kernel_description": "#1 SMP PVE 5.4.162-2 (Thu, 20 Jan 2022 16:38:53 +0100)",
"kernel_version": "5.4.162-1-pve",
"mem_swap_kb": "8388604",
"mem_total_kb": "65747752",
"os": "Linux"
},
{
"name": "pxceph2",
"addrs": "[v2:10.10.20.21:3300/0,v1:10.10.20.21:6789/0]",
"arch": "x86_64",
"ceph_release": "nautilus",
"ceph_version": "ceph version 14.2.22 (877fa256043e4743620f4677e72dee5e738d1226) nautilus (stable)",
"ceph_version_short": "14.2.22",
"compression_algorithms": "none, snappy, zlib, zstd, lz4",
"cpu": "Intel(R) Xeon(R) CPU E5-1650 v4 @ 3.60GHz",
"device_ids": "",
"device_paths": "",
"devices": "",
"distro": "debian",
"distro_description": "Debian GNU/Linux 10 (buster)",
"distro_version": "10",
"hostname": "pxceph2",
"kernel_description": "#1 SMP PVE 5.4.162-2 (Thu, 20 Jan 2022 16:38:53 +0100)",
"kernel_version": "5.4.162-1-pve",
"mem_swap_kb": "8388604",
"mem_total_kb": "65747752",
"os": "Linux"
},
{
"name": "pxceph3",
"addrs": "[v2:10.10.20.22:3300/0,v1:10.10.20.22:6789/0]",
"arch": "x86_64",
"ceph_release": "nautilus",
"ceph_version": "ceph version 14.2.22 (877fa256043e4743620f4677e72dee5e738d1226) nautilus (stable)",
"ceph_version_short": "14.2.22",
"compression_algorithms": "none, snappy, zlib, zstd, lz4",
"cpu": "Intel(R) Xeon(R) CPU E5-1650 v4 @ 3.60GHz",
"device_ids": "",
"device_paths": "",
"devices": "",
"distro": "debian",
"distro_description": "Debian GNU/Linux 10 (buster)",
"distro_version": "10",
"hostname": "pxceph3",
"kernel_description": "#1 SMP PVE 5.4.162-2 (Thu, 20 Jan 2022 16:38:53 +0100)",
"kernel_version": "5.4.162-1-pve",
"mem_swap_kb": "8388604",
"mem_total_kb": "65747752",
"os": "Linux"
}
]