I have been backing up to PBS for a few weeks. The backup job contains 3 VMs. THe first one was backed up correctly the next 2 failed with this error:
in this code you can see the end of the backup of the first VM followed by the error.
Any ideas what this means?
This is quite baffling a PVE and PBS are both running on the same host.
in this code you can see the end of the backup of the first VM followed by the error.
Code:
INFO: 97% (18.6 GiB of 19.1 GiB) in 4m 57s, read: 85.3 MiB/s, write: 50.7 MiB/s
INFO: 98% (18.8 GiB of 19.1 GiB) in 5m 0s, read: 60.0 MiB/s, write: 20.0 MiB/s
INFO: 100% (19.1 GiB of 19.1 GiB) in 5m 3s, read: 113.3 MiB/s, write: 96.0 MiB/s
INFO: backup is sparse: 1004.00 MiB (5%) total zero data
INFO: backup was done incrementally, reused 142.89 GiB (89%)
INFO: transferred 19.12 GiB in 308 seconds (63.6 MiB/s)
INFO: Finished Backup of VM 100 (00:05:14)
INFO: Backup finished at 2021-02-12 01:20:15
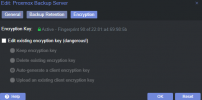
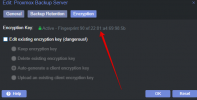
Using encryption key from file descriptor
ERROR: Backup job failed - upload log failed: Error: KeyConfig contains wrong fingerprint FINGERPRINTA, contained key has fingerprint FINGERPRINTBAny ideas what this means?
This is quite baffling a PVE and PBS are both running on the same host.
Last edited: