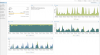
Thank you @heutger Here is my second day update of Disabling SPF and Graylisting - Well we are processing mails faster, that is for sure - the wait for Graylist is over, but we got a lot more spam today that was failing because of SPF. Thanks to invaluement - I increased the Score a bit, and I also added the
I had a question for @Stoiko Ivanov @ittk and you - what is your average time to process a mail - I stand somewhere in the middle of 3 to 4 seconds, with a 4 GB RAM, 2 Virtual core machine - and about 10,000 Peak traffic emails a day. I am also continuing to publish more and more of my Blacklists as Spam Asassin rules similar to what sachal@it and KAM have done - this is helping reduce some COVID related spam that we are seeing on the rise.
problems.dnsbl.sorbs.net in my second line of defence with a 2 Score, this has helped bring the SPAM down a bit. I still continue to work on improving it.I had a question for @Stoiko Ivanov @ittk and you - what is your average time to process a mail - I stand somewhere in the middle of 3 to 4 seconds, with a 4 GB RAM, 2 Virtual core machine - and about 10,000 Peak traffic emails a day. I am also continuing to publish more and more of my Blacklists as Spam Asassin rules similar to what sachal@it and KAM have done - this is helping reduce some COVID related spam that we are seeing on the rise.