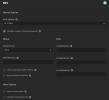
Hello,
I have an up-to-date TrueNAS SCALE bare metal server running that I'm using to, among other things, store LXC templates and ISOs for Proxmox. I initially configured TrueNAS's NFS service to disable NFS v3, as I knew Proxmox supported v4.2 and that's what I wanted to use.
However, Proxmox was only able to see the server, but not list exported shares of the NFS v4-only server. I had to re-enable the NFSv3 protocol on the server to get the share list working again so Proxmox could connect to it within the GUI, even when explicitly telling Proxmox to use NFS 4.2.
At first I thought I'd broken my TrueNAS server's NFS implementation somehow, and went on a fun troubleshooting journey and even filed my first TrueNAS bug report. See: https://forums.truenas.com/t/truenas-scale-dragonfish-24-04-1-1-nfs-service-not-working/7612
tl;dr NFS v4 does not support the
I wanted to confirm that is how PVE's web interface for adding NFS shares actually works. If it's not, I don't know what's causing this issue.
Also, while it's not a bug, it's definitely confusing if you're using NFS for the first time. Proxmox was the first time I needed to use an NFS share; I'd always used SMB before that, and disabling older versions of SMB doesn't impact the functionality of the version of SMB you're actually using. That said, I'm considering filing a bug to request a help popup/expansion somewhere appropriate in the Add NFS dialogue box to indicate that NFS is required. I spent nearly 3 hours troubleshooting an NFS server that was working correctly and would like to find a way to help other people not do that.
I have an up-to-date TrueNAS SCALE bare metal server running that I'm using to, among other things, store LXC templates and ISOs for Proxmox. I initially configured TrueNAS's NFS service to disable NFS v3, as I knew Proxmox supported v4.2 and that's what I wanted to use.
However, Proxmox was only able to see the server, but not list exported shares of the NFS v4-only server. I had to re-enable the NFSv3 protocol on the server to get the share list working again so Proxmox could connect to it within the GUI, even when explicitly telling Proxmox to use NFS 4.2.
At first I thought I'd broken my TrueNAS server's NFS implementation somehow, and went on a fun troubleshooting journey and even filed my first TrueNAS bug report. See: https://forums.truenas.com/t/truenas-scale-dragonfish-24-04-1-1-nfs-service-not-working/7612
tl;dr NFS v4 does not support the
showmount command. If Proxmox is relying on this command to list the available exported shares when adding an NFS share at the cluster level, it will fail if the server has NFS v3 disabled.I wanted to confirm that is how PVE's web interface for adding NFS shares actually works. If it's not, I don't know what's causing this issue.
Also, while it's not a bug, it's definitely confusing if you're using NFS for the first time. Proxmox was the first time I needed to use an NFS share; I'd always used SMB before that, and disabling older versions of SMB doesn't impact the functionality of the version of SMB you're actually using. That said, I'm considering filing a bug to request a help popup/expansion somewhere appropriate in the Add NFS dialogue box to indicate that NFS is required. I spent nearly 3 hours troubleshooting an NFS server that was working correctly and would like to find a way to help other people not do that.