Hello,
I'm getting my first proxmox system online (Broadcom/VMware victim). I'm quite impressed thus far with the ease of pulling in VMs from VMware systems and the setup/performance compared to VMware.
Anyways, I had a quick question:
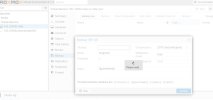
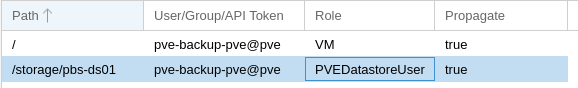
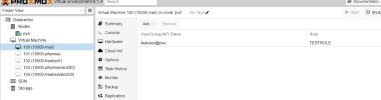
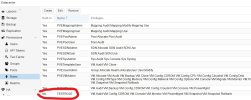
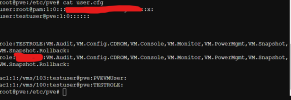
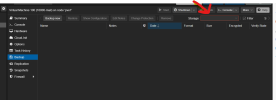
I created a very basic role that includes: VM.Audit VM.Config VM.CDROM VM.Console VM.Monitor VM.PowerMgmt VM.Snapshot VM.Snapshot.Rollback. As a user with these permissions, if I click on Backup I'm presented with the Backup screen and the "Backup Now" button. If the "Backup Now" button is pressed it freezes the browser with a "please wait" screen. The only way out of it is to refresh the browser. I'm assuming this is normal. If this is normal, shouldn't the user (without VM.Backup) be prevented from getting into this situation in the first place? e.g. No ability to enter the backup section or simply not able to click "Backup Now".
I'm getting my first proxmox system online (Broadcom/VMware victim). I'm quite impressed thus far with the ease of pulling in VMs from VMware systems and the setup/performance compared to VMware.
Anyways, I had a quick question:
I created a very basic role that includes: VM.Audit VM.Config VM.CDROM VM.Console VM.Monitor VM.PowerMgmt VM.Snapshot VM.Snapshot.Rollback. As a user with these permissions, if I click on Backup I'm presented with the Backup screen and the "Backup Now" button. If the "Backup Now" button is pressed it freezes the browser with a "please wait" screen. The only way out of it is to refresh the browser. I'm assuming this is normal. If this is normal, shouldn't the user (without VM.Backup) be prevented from getting into this situation in the first place? e.g. No ability to enter the backup section or simply not able to click "Backup Now".
Attachments
Last edited: