Hello all
I've been searching throughout the forum for few days and found several threads related to this topic but each of them was missing some small piece of information which could lead me to the resolution of my issue.
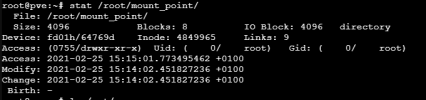
Briefly this is my current configuration: ProxMox virtual server with an usb hub where I installed 5 hard drives. All of them have been mounted to the host via fstab using their respective uuids. This is working ok so far. I'm now in the need of creating a mount point in one container (unprivileged) and I get the write permission issue as expected.
Now, looking at the options I have I'd like to do what it's written here but I'm stuck at the point where I have to enter the right uid and gid. Wtihin the host I have only the root user and the same goes within the container, so I'd simply be able to use the root user in the container and write to the mount point using that.
Should it be something like this?
I've been searching throughout the forum for few days and found several threads related to this topic but each of them was missing some small piece of information which could lead me to the resolution of my issue.
Briefly this is my current configuration: ProxMox virtual server with an usb hub where I installed 5 hard drives. All of them have been mounted to the host via fstab using their respective uuids. This is working ok so far. I'm now in the need of creating a mount point in one container (unprivileged) and I get the write permission issue as expected.
Now, looking at the options I have I'd like to do what it's written here but I'm stuck at the point where I have to enter the right uid and gid. Wtihin the host I have only the root user and the same goes within the container, so I'd simply be able to use the root user in the container and write to the mount point using that.
Should it be something like this?
Code:
# Add to /etc/pve/lxc/<container_id>.conf:
lxc.idmap: u 0 100000 0
lxc.idmap: g 0 100000 0
lxc.idmap: u 0 0 1
lxc.idmap: g 0 0 1
lxc.idmap: u 1 100109 65427
lxc.idmap: g 1 100115 65421
# Add to /etc/subuid:
root:0:1
# Add to /etc/subgid:
root:0:1