Hello all
finally had time to try it out and after many attempts I think I figured it out. I have a CT user with UID 110 and GID 117 and that's how I mapped it:
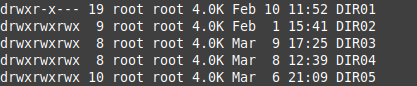
The CT started and seemed to work fine, but the service which is starting with that UID now fails to start. It returns permission denied message:
How is the mapping affecting the container permissions? I mean, from what I understood, by mapping the UID and GID you only affect what you do outside the container, isn't it?
finally had time to try it out and after many attempts I think I figured it out. I have a CT user with UID 110 and GID 117 and that's how I mapped it:
Code:
lxc.idmap: u 0 100000 110
lxc.idmap: g 0 100000 117
lxc.idmap: u 110 110 1
lxc.idmap: g 117 117 1
lxc.idmap: u 111 100111 65425
lxc.idmap: g 118 100118 65417The CT started and seemed to work fine, but the service which is starting with that UID now fails to start. It returns permission denied message:
Unhandled exception. System.UnauthorizedAccessException: Access to the path '/var/lib/jellyfin/data' is denied.
How is the mapping affecting the container permissions? I mean, from what I understood, by mapping the UID and GID you only affect what you do outside the container, isn't it?