Hi there,
I would like to access to my pfSense via the webGUI, but after reading all different kind of things, I have no clue how to do this sadly
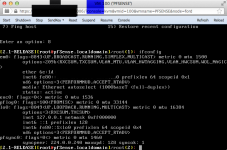
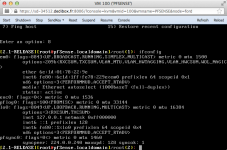
My interface file looks like this.
In the pfSense install I gave em0 as the WAN interface and the em1 as the local one. Only the local one has an IP of 192.168.1.1
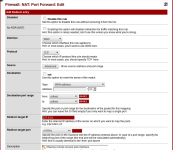
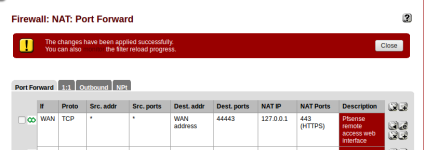
Please not as well that my ProxMox has one public address (8x.1x.3x.2x). So how can I access to the pfSense server for the webgui and as well ssh, as I cannot go from my proxmox server to 192.168.1.1
Thank you in advance for any help you can give.
I would like to access to my pfSense via the webGUI, but after reading all different kind of things, I have no clue how to do this sadly
My interface file looks like this.
Code:
# This file describes the network interfaces available on your system# and how to activate them. For more information, see interfaces(5).
# The loopback network interface
auto lo
iface lo inet loopback
# The primary network interface
auto vmbr0
iface vmbr0 inet static
address 8x.1x.3x.2x
netmask 255.255.255.0
network 8x.1x.3x.0
broadcast 8x.1x.3x.255
gateway 8x.1x.3x.1
bridge_ports eth0
bridge_stp on
bridge_fd 0
## this is for the DMZ - Pfsense
auto vmbr10
iface vmbr10 inet manual
bridge_ports eth1
bridge_stp off
bridge_fd 0In the pfSense install I gave em0 as the WAN interface and the em1 as the local one. Only the local one has an IP of 192.168.1.1
Please not as well that my ProxMox has one public address (8x.1x.3x.2x). So how can I access to the pfSense server for the webgui and as well ssh, as I cannot go from my proxmox server to 192.168.1.1
Thank you in advance for any help you can give.