Version: 8.3.5
Problem:
The vm inside sees the configured MAC address off it's interface , so infos are passed to the vm. But the vm can't send data outside.
Even with a correct configured ip / netmask and route inside the vm, tcpdump can't see any traffic what so ever on the fw* interfaces below:
btw: sorry for using <CLASSB> as a visual protection.
sysctl.conf
net.ipv4.ip_forward=1
when the vm is running, the interfaces are created:
They vanish, if the vm is stopped.
interface config:
The up route rule was taken to vmbr0 , because the enp41s0 interface was configured by the setup script as the primary interface without a bridge.
I had to create a vmbr0 via UI and change the interfaces.new file to move the rule to the vmbr0 block.
default via <CLASSB>.54.1 dev vmbr0 proto kernel onlink
<CLASSB>.54.0/26 via <CLASSB>.54.1 dev vmbr0
<CLASSB>.54.0/26 dev vmbr0 proto kernel scope link src <CLASSB>.54.34
I have another PVE, but that did not need have this rule, I assume its obsolete anyway:
<CLASSB>.54.0/26 via <CLASSB>.54.1 dev vmbr0
even if it would do something, it can't stop traffic from the vm to disappear on the created fw* interfaces.
I knew, i had such a problem with a bridge before (not pve), but i can't remember how to fix this.
Problem:
The vm inside sees the configured MAC address off it's interface , so infos are passed to the vm. But the vm can't send data outside.
Even with a correct configured ip / netmask and route inside the vm, tcpdump can't see any traffic what so ever on the fw* interfaces below:
btw: sorry for using <CLASSB> as a visual protection.
sysctl.conf
net.ipv4.ip_forward=1
when the vm is running, the interfaces are created:
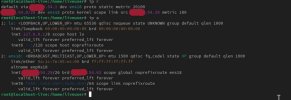
Code:
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
2: enp41s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master vmbr0 state UP mode DEFAULT group default qlen 1000
link/ether a8:a1:59:c0:d0:c0 brd ff:ff:ff:ff:ff:ff
3: vmbr0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP mode DEFAULT group default qlen 1000
link/ether a8:a1:59:c0:d0:c0 brd ff:ff:ff:ff:ff:ff
4: tap104i0: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master fwbr104i0 state UNKNOWN mode DEFAULT group default qlen 1000
link/ether ce:b0:82:ad:33:b6 brd ff:ff:ff:ff:ff:ff
5: fwbr104i0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP mode DEFAULT group default qlen 1000
link/ether aa:2b:30:36:e2:b6 brd ff:ff:ff:ff:ff:ff
6: fwpr104p0@fwln104i0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master vmbr0 state UP mode DEFAULT group default qlen 1000
link/ether de:ef:67:c0:c1:17 brd ff:ff:ff:ff:ff:ff
7: fwln104i0@fwpr104p0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master fwbr104i0 state UP mode DEFAULT group default qlen 1000
link/ether aa:2b:30:36:e2:b6 brd ff:ff:ff:ff:ff:ffThey vanish, if the vm is stopped.
interface config:
Code:
auto lo
iface lo inet loopback
iface lo inet6 loopback
auto enp41s0
iface enp41s0 inet manual
iface eth0 inet manual
auto vmbr0
iface vmbr0 inet static
address <CLASSB>.54.34/26
gateway <CLASSB>.54.1
bridge-ports enp41s0
bridge-stp off
bridge-fd 0
up route add -net <CLASSB>.54.0 netmask 255.255.255.192 gw <CLASSB>.54.1 dev vmbr0
iface vmbr0 inet6 static
address IPV6ADDR:2/64
gateway fe80::1The up route rule was taken to vmbr0 , because the enp41s0 interface was configured by the setup script as the primary interface without a bridge.
I had to create a vmbr0 via UI and change the interfaces.new file to move the rule to the vmbr0 block.
default via <CLASSB>.54.1 dev vmbr0 proto kernel onlink
<CLASSB>.54.0/26 via <CLASSB>.54.1 dev vmbr0
<CLASSB>.54.0/26 dev vmbr0 proto kernel scope link src <CLASSB>.54.34
I have another PVE, but that did not need have this rule, I assume its obsolete anyway:
<CLASSB>.54.0/26 via <CLASSB>.54.1 dev vmbr0
even if it would do something, it can't stop traffic from the vm to disappear on the created fw* interfaces.
I knew, i had such a problem with a bridge before (not pve), but i can't remember how to fix this.