anyone can confirm that this works, with manual verification from the datacenter support?3) echo 0 >/proc/sys/net/ipv4/igmp_link_local_mcast_reports + add in /etc/sysctl.d/pve.conf
"net.ipv4.igmp_link_local_mcast_reports = 0"
Proxmox claiming MAC address
- Thread starter tmsg
- Start date
-
- Tags
- networking openvswitch ovs
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
It doesn't. Well at least it never worked for me. I applied this and msged DC support - they said it's fine and they don't see any wrong MAC traffic, but after a few days - same story. So the issue comes and goes.anyone can confirm that this works, with manual verification from the datacenter support?
Today they even locked my server (!!!). I applied a firewall rule as suggested here and it was unblocked. Again traffic is said as clean. We'll see how it goes now...
so, just to be sure, do you apply all theses fixes:It doesn't. Well at least it never worked for me. I applied this and msged DC support - they said it's fine and they don't see any wrong MAC traffic, but after a few days - same story. So the issue comes and goes.
Today they even locked my server (!!!). I applied a firewall rule as suggested here and it was unblocked. Again traffic is said as clean. We'll see how it goes now...
Code:
1) never use REJECT rules for inbound rules, and use DROP as default action.
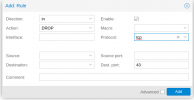
2) if you are still on proxmox6, add an extra DROP for tcp/43 for inbound rule. (this is fixed in proxmox7 pve-firewall_4.2-3 )
3) echo 0 >/proc/sys/net/ipv4/igmp_link_local_mcast_reports + add in /etc/sysctl.d/pve.conf
"net.ipv4.igmp_link_local_mcast_reports = 0"?
do you have any logs from hetzner about the wrong mac or ip ?
(I would like to known if the mac is a mac of a specific device on proxmox (tap,fwbr,...), and if ip is an ip from proxmox host too)
Code:1) never use REJECT rules for inbound rules, and use DROP as default action. 2) if you are still on proxmox6, add an extra DROP for tcp/43 for inbound rule. (this is fixed in proxmox7 pve-firewall_4.2-3 ) 3) echo 0 >/proc/sys/net/ipv4/igmp_link_local_mcast_reports + add in /etc/sysctl.d/pve.conf "net.ipv4.igmp_link_local_mcast_reports = 0"
1. Never used REJECT at all.
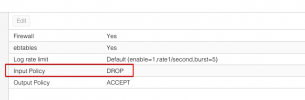
2. I have this as the default rule on datacenter level:
3. Done long time ago
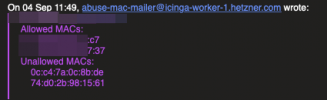
It seems to be random different MACs all the time, here are examples of abuse messages:?
do you have any logs from hetzner about the wrong mac or ip ?
(I would like to known if the mac is a mac of a specific device on proxmox (tap,fwbr,...), and if ip is an ip from proxmox host too)
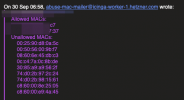
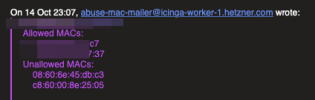
Last edited:
I received my fifth abuse message today:
On 26 Oct 01:37, abuse-mac-mailer@icinga-worker-1.hetzner.com wrote:
On 26 Oct 01:37, abuse-mac-mailer@icinga-worker-1.hetzner.com wrote:
#1011951 (138.201.52.41)
Allowed MACs:
00:50:56:15:24:cc
00:50:56:15:24:9b
90:1b:0e:91:c2:ba
00:50:56:00:4d:d0
00:50:56:00:3f:4e
00:50:56:00:2b:66
00:50:56:00:37:8a
Unallowed MACs:
46:0c:af:0e:36:55
c6:81:b4:a8:ad:21
datacenter rules only apply to host firewall , not vm firewall.2. I have this as the default rule on datacenter level:
View attachment 30792
do you have drop input policy on every vm firewall option ?
and if yes, do you use proxmox7 with last pve-firewall updates ? or if proxmox6, do you have added a "drop port 43" for every vm ?
I still run Proxmox 6. On the mentioned host it's only one VM running with the following configuration of the firewall:datacenter rules only apply to host firewall , not vm firewall.
do you have drop input policy on every vm firewall option ?
and if yes, do you use proxmox7 with last pve-firewall updates ? or if proxmox6, do you have added a "drop port 43" for every vm ?
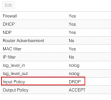
SMALL UPDATE: For the sake of completeness... The host has two VMs that have Firewall disabled, but those VMs are being used as a template for other hosts and were never up. I don't believe it can be an issue.
Last edited:
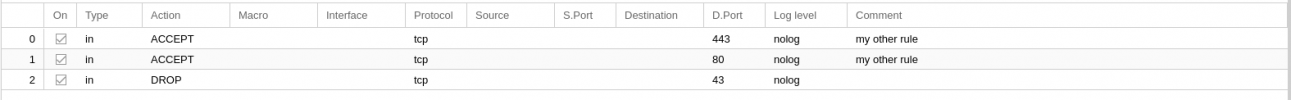
if you are on proxmox6, you need to add a rule to drop port tcp 43 direction in, at the end of your vms rules (for each vm where is firewall is enabled).I still run Proxmox 6. On the mentioned host it's only one VM running with the following configuration of the firewall:
View attachment 30802
SMALL UPDATE: For the sake of completeness... The host has two VMs that have Firewall disabled, but those VMs are being used as a template for other hosts and were never up. I don't believe it can be an issue.
They are a bug in default input policy DROP, where a reject is done for port tcp43. (it's fixed in proxmox7 last version).
About template it's not a problem, as they are not running.
no news?
I need to setup a new proxmox server, and hetzner is the best cheap datacenter ....
how to do with this situation?
I need to setup a new proxmox server, and hetzner is the best cheap datacenter ....
how to do with this situation?
no one of all proposed solutions works for me. I have switched to AWS for critical live streaming application. but is too expensive.i have the same issue with hetzner, did the command above solved the issue for you?
I need to use an hardware server with flat network.
it's not good choice to go aws/azure they are very expensiveno one of all proposed solutions works for me. I have switched to AWS for critical live streaming application. but is too expensive.
I need to use an hardware server with flat network.
if both solutions (iptables drop port 43 + drop default action (and no reject rules) + sysctl to drop igmp local link) don't work, maybe it's another bug.no one of all proposed solutions works for me. I have switched to AWS for critical live streaming application. but is too expensive.
I need to use an hardware server with flat network.
(but I'm 99% sure that your hetzner lock when vm is stop/start is coming from igmp local link)
I really need to have some trace with:
Code:
ebtables -I OUTPUT -o <phyiscal intertace> --among-src ! <mac1,mac2,mac3....> --log-level info --log-prefix "MAC-FLOOD-O" --log-ip -j CONTINUE
ebtables -I FORWARD -o <physical interface> --among-src ! <mac1,mac2,mac3....> --log-level info --log-prefix "MAC-FLOOD-F" --log-ip -j CONTINUEdon't drop, only log. if lock occur at hetzner, we'll be able to compare mac from hetzner side, with the detailed log on proxmox side.
did you ask for manual MAC verification from network support? i also went weeks without warnings .. then asking for manual scan .. the problem was always there ..I was helped by the solutions that Spirit provided. Messages from Hetzner had never been received again for three weeks. Thanks!
Also did you do some server and vps reboots?
Last edited:
I didn't ask for a manual check, but the server has restarted many times.
Unfortunately, more than three weeks later, I received the message again. And this time the number of unallowed MACs was 9. And I did not find any of them on my system, but before I could find them using the command: "bridge fdb show". There may be a problem in installing a new virtual machine with the control panel Hestia CP. I did not take any other actions.
But I am using Proxmox 6 and may be adding a DROP rule at the end of my rules incorrectly. How am I supposed to do it right?
Unfortunately, more than three weeks later, I received the message again. And this time the number of unallowed MACs was 9. And I did not find any of them on my system, but before I could find them using the command: "bridge fdb show". There may be a problem in installing a new virtual machine with the control panel Hestia CP. I did not take any other actions.
But I am using Proxmox 6 and may be adding a DROP rule at the end of my rules incorrectly. How am I supposed to do it right?
Last edited:
Looking for others Companies guides about proxmox networking I see that ovh official guide use the IP routed setup mode instead of bridged.
https://docs.ovh.com/gb/en/dedicated/network-bridging/
https://docs.ovh.com/gb/en/dedicated/network-bridging/