Hello,
I'm new to proxmox and hypervisors of this type. So far I've been self-hosting for very simple services or using devices like yunohost.
I've made the sketch below to visualize the infrastructure I want to set up:
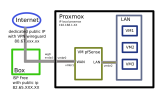
I've already installed proxmoxve8 and configured a wireguard wg0 VPN tunnel as a client directly on the proxmox machine. This tunnel seems to be working, I've managed to ping it and the vpn's ip address (and not the public ip of the box) is returned to me when I query online services.
But when I created a VM connected to the interface created by default vmbrO, this vm had the ip address of the freebox 82.65.XXX.XX and not those of the vpn (80.67.XXX.XX).
I'd like my future LAN's network traffic to pass through the VPN wireguard wg0 tunnel, so that the services available on the LAN's VMs can be contacted via the VPN's ip (80.67.XXX.XX) (and not the box ip 82.65.XXX.XX).
Is it possible to create a vmbr network interface configured with the VPN's public ip (80.67.XXX.XX)?
Or maybe I'm going the wrong way and need to do something different?
What do you think?
Thanks for your help and sorry for my bad English!
Bilm
I'm new to proxmox and hypervisors of this type. So far I've been self-hosting for very simple services or using devices like yunohost.
I've made the sketch below to visualize the infrastructure I want to set up:

I've already installed proxmoxve8 and configured a wireguard wg0 VPN tunnel as a client directly on the proxmox machine. This tunnel seems to be working, I've managed to ping it and the vpn's ip address (and not the public ip of the box) is returned to me when I query online services.
But when I created a VM connected to the interface created by default vmbrO, this vm had the ip address of the freebox 82.65.XXX.XX and not those of the vpn (80.67.XXX.XX).
I'd like my future LAN's network traffic to pass through the VPN wireguard wg0 tunnel, so that the services available on the LAN's VMs can be contacted via the VPN's ip (80.67.XXX.XX) (and not the box ip 82.65.XXX.XX).
Is it possible to create a vmbr network interface configured with the VPN's public ip (80.67.XXX.XX)?
Or maybe I'm going the wrong way and need to do something different?
What do you think?
Thanks for your help and sorry for my bad English!
Bilm

