Hello,
I'm trying to troubleshoot an issue we have win a windows VM which periodically has trouble accessing disks.
In the windows system log, I can see that some attached disks (not always the same) starts being resetted by the vioscsi driver.
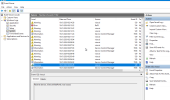
The result is that in the VM the mounted disk is inaccessible and any attempt to access the disk result in freezing explorer, etc. The only solution is to kill the VM (hard stop) and start it again.
Proxmox version is the latest.
The VM runs Win 2022 and exchange server 2019 ans has a system disk and 8 others disks attached for Exchange databases + Exchanges databases transaction logs formatted in ReFS as suggested by MS. The VM has the latest Win virtio guest tools installed.
The disks are qcow2 files hosted on a NFS share on a quite powerfull Huawei SAN/NAS. I have not noticed any performance issue with the VM images file storage.
The full VM config is here:
Still, I also notice that the vioscsi resets begins to occurs a bit after the scheduled Proxmox backups to a PBS occurs, but the issue happens not every night when the backups are running every night.
I had read that backups can be heavy on IO though and there were suggestion to lower the IO agressivity, so I went ahead and set these settings (performance and ionice)
Still the issue remains and we have no choice than to kill the VM as a normal shutdown will be stuck on waiting for disk access...
Then we lose CBT for the VM and the next backup will need a full read of the disks....
Any suggestion or ideas about what else I could try to troubleshoot to find the origin of the issue is welcome.
Thanks a lot !
I'm trying to troubleshoot an issue we have win a windows VM which periodically has trouble accessing disks.
In the windows system log, I can see that some attached disks (not always the same) starts being resetted by the vioscsi driver.

The result is that in the VM the mounted disk is inaccessible and any attempt to access the disk result in freezing explorer, etc. The only solution is to kill the VM (hard stop) and start it again.
Proxmox version is the latest.
The VM runs Win 2022 and exchange server 2019 ans has a system disk and 8 others disks attached for Exchange databases + Exchanges databases transaction logs formatted in ReFS as suggested by MS. The VM has the latest Win virtio guest tools installed.
The disks are qcow2 files hosted on a NFS share on a quite powerfull Huawei SAN/NAS. I have not noticed any performance issue with the VM images file storage.
The full VM config is here:
Code:
agent: 1
balloon: 0
bios: ovmf
boot: order=scsi0
cores: 8
cpu: SandyBridge
efidisk0: Huawei_NFS:404/vm-404-disk-0.qcow2,efitype=4m,pre-enrolled-keys=1,size=528K
machine: pc-q35-8.1
memory: 32768
meta: creation-qemu=8.0.2,ctime=1692075358
name: exchange22019
net0: virtio=9E:4A:1F:20:27:A1,bridge=vmbr0,firewall=1,tag=12
numa: 0
onboot: 1
ostype: win11
protection: 1
scsi0: Huawei_NFS:404/vm-404-disk-1.qcow2,cache=writeback,discard=on,iothread=1,size=150G,ssd=1
scsi1: Huawei_NFS:404/vm-404-disk-4.qcow2,cache=writeback,discard=on,iothread=1,size=500G,ssd=1
scsi2: Huawei_NFS:404/vm-404-disk-5.qcow2,cache=writeback,discard=on,iothread=1,size=500G,ssd=1
scsi3: Huawei_NFS:404/vm-404-disk-6.qcow2,cache=writeback,discard=on,iothread=1,size=500G,ssd=1
scsi4: Huawei_NFS:404/vm-404-disk-7.qcow2,cache=writeback,discard=on,iothread=1,size=500G,ssd=1
scsi5: Huawei_NFS:404/vm-404-disk-8.qcow2,cache=writeback,discard=on,iothread=1,size=20G,ssd=1
scsi6: Huawei_NFS:404/vm-404-disk-9.qcow2,cache=writeback,discard=on,iothread=1,size=20G,ssd=1
scsi7: Huawei_NFS:404/vm-404-disk-10.qcow2,cache=writeback,discard=on,iothread=1,size=20G,ssd=1
scsi8: Huawei_NFS:404/vm-404-disk-11.qcow2,cache=writeback,discard=on,iothread=1,size=20G,ssd=1
scsihw: virtio-scsi-single
smbios1: uuid=25dc92bb-9161-4df1-bb54-a9d87674366c
sockets: 1
vmgenid: 8587649c-8b96-49bf-837e-878349ff8421Still, I also notice that the vioscsi resets begins to occurs a bit after the scheduled Proxmox backups to a PBS occurs, but the issue happens not every night when the backups are running every night.
I had read that backups can be heavy on IO though and there were suggestion to lower the IO agressivity, so I went ahead and set these settings (performance and ionice)
Code:
root@pm:~# cat /etc/vzdump.conf
# vzdump default settings
performance: max-workers=1
ionice: 8
#tmpdir: DIR
#dumpdir: DIR
#storage: STORAGE_ID
#mode: snapshot|suspend|stop
#bwlimit: KBPS
#performance: [max-workers=N][,pbs-entries-max=N]
#lockwait: MINUTES
#stopwait: MINUTES
#stdexcludes: BOOLEAN
#mailto: ADDRESSLIST
#prune-backups: keep-INTERVAL=N[,...]
#script: FILENAME
#exclude-path: PATHLIST
#pigz: N
#notes-template: {{guestname}}Still the issue remains and we have no choice than to kill the VM as a normal shutdown will be stuck on waiting for disk access...
Then we lose CBT for the VM and the next backup will need a full read of the disks....
Any suggestion or ideas about what else I could try to troubleshoot to find the origin of the issue is welcome.
Thanks a lot !

