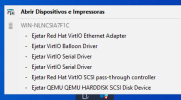
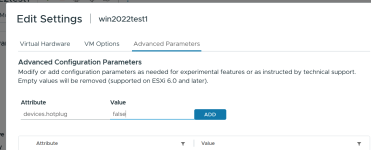
[h=3]Situation[/h] We belive due to an older SEABIOS version in Proxmox our Windows VM's 7 + 2008 servers have the ability to 'Safely remove' critical hardware like the disk and network cards. This is down to the Seabios having hot-swappable PCI enabled.
Could be related to
"
BZ#671544 On a Windows virtual machine it was possible to 'Safely Remove' too many devices, including the graphics adapter, the PCI to ISA bridge device, and the PCI RAM controller, resulting in system instability. This patch uses the _RMV method to indicate whether device can be removed, thus fixing the issue.
"
from https://access.redhat.com/site/docu...Linux/6/html/6.1_Technical_Notes/seabios.html
[h=3]Our 'Fix'[/h]Create a batch file based on the below contents and use Group Policy to run it on start-up
[h=3]Procedure[/h] The below assumes that the SCSI controller, Virtio Balloon Driver and E1000 Network Card are able to be ejected
Open Device Manager
Right click your device, left click properties
Click Details Tab and from that drop down select "Device Instance Path"
Either note this down! or leave on screen as you will need it shortly
:: Original value: 6
reg.exe add "PLACEHOLDER" /v Capabilities /t REG_DWORD /d 2 /f
:: Disable eject ballon
:: Original value: 6
reg.exe add "PLACEHOLDER" /v Capabilities /t REG_DWORD /d 2 /f
:: Disable eject network card
:: Original value: 6
reg.exe add "PLACEHOLDER" /v Capabilities /t REG_DWORD /d 2 /f
Important when in the registry editor, look under the Capabilities sextion and check it ends with 6 (ie 0x00000006) if it doesn't the the corresponding entry in your notpad instance nust be changed to four less than that value. ie if the Capabilities section read 0x00000007 you would change the line from /d 2 to /d 3
Notes:
This workaround is a little time consuming and it would seem that a newer Seabios would solve it.
Posting this just to get your thoughts and help anyone that finds themselves in our shoes.
Could be related to
"
BZ#671544 On a Windows virtual machine it was possible to 'Safely Remove' too many devices, including the graphics adapter, the PCI to ISA bridge device, and the PCI RAM controller, resulting in system instability. This patch uses the _RMV method to indicate whether device can be removed, thus fixing the issue.
"
from https://access.redhat.com/site/docu...Linux/6/html/6.1_Technical_Notes/seabios.html
[h=3]Our 'Fix'[/h]Create a batch file based on the below contents and use Group Policy to run it on start-up
[h=3]Procedure[/h] The below assumes that the SCSI controller, Virtio Balloon Driver and E1000 Network Card are able to be ejected
Open Device Manager
Right click your device, left click properties
Click Details Tab and from that drop down select "Device Instance Path"
Either note this down! or leave on screen as you will need it shortly
- Open notepad (or preferred editor)
- Copy in below contents
:: Original value: 6
reg.exe add "PLACEHOLDER" /v Capabilities /t REG_DWORD /d 2 /f
:: Disable eject ballon
:: Original value: 6
reg.exe add "PLACEHOLDER" /v Capabilities /t REG_DWORD /d 2 /f
:: Disable eject network card
:: Original value: 6
reg.exe add "PLACEHOLDER" /v Capabilities /t REG_DWORD /d 2 /f
- Run Regedit
- Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum
- Search for your device and right lick on the key '3&13c0b0c5&0&XX' or similar and select 'Copy Key Name'
- Use this Copied key name in your notepad instance we have just stated in place of PLACEHOLDER. THe line should now look like
Important when in the registry editor, look under the Capabilities sextion and check it ends with 6 (ie 0x00000006) if it doesn't the the corresponding entry in your notpad instance nust be changed to four less than that value. ie if the Capabilities section read 0x00000007 you would change the line from /d 2 to /d 3
- Once all eject-able devices have been added save the file as a .bat in a safe place and open the group policy editor.
- >Computer Configuration
- >Windows Settings
- Scripts (Startup/Shutdown)
- Double Click Startup and add your script to the list.
- Reboot
- Smile
Notes:
This workaround is a little time consuming and it would seem that a newer Seabios would solve it.
Posting this just to get your thoughts and help anyone that finds themselves in our shoes.