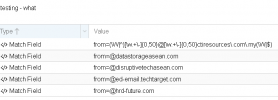
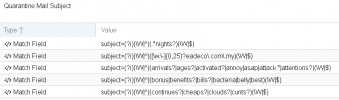
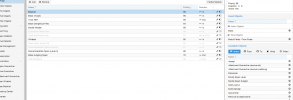
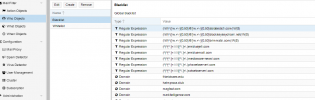
OK, I deleted the what object, but FYI I added it when the who didn't work.
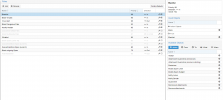
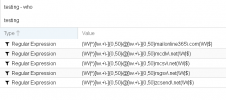
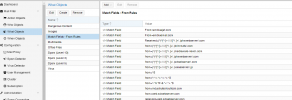
Rules attached, I believe I left those at the default values.
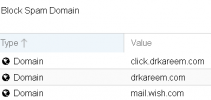
** after applying the rules as requested, continued to receive messages with that sender.
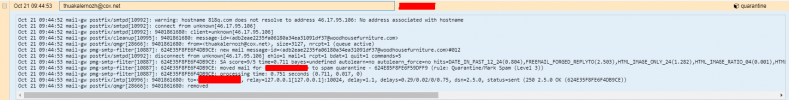
Header attached.
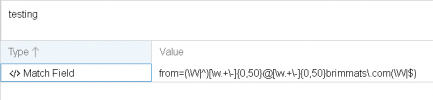
** received another this morning with FC7LX.R3OFC7LX@1JSV.brimmats.com when I test that in the regex it matches, but not sure yet since I havent been using PMG long the reason why it's not being rejected.
Todays header (AM):
Delivered-To: andrew@test.net
Return-Path:
Received: from email.seattle.gov (senke.deparench.eu [89.251.16.110])
by mgw.localdomain (Proxmox) with ESMTP id 37AEB809F1
for <andrew@test.net>; Mon, 12 Oct 2020 09:38:42 -0400 (EDT)
subject: SPAM: Say Bye To Moles And SkinTags
From: "DermaCorrect Skin Tags" <R3OFC7LX.R3OFC7LX@1JSV.brimmats.com>
To: alicia@web56.net
Content-Type: text/html; charset=utf-8;
Content-Disposition: inline
Date: Mon, 12 Oct 2020 09:00:48 -0400
X-SPAM-LEVEL: Spam detection results: 16
BODY_URI_ONLY 0.822 Message body is only a URI in one line of text or for an image
FSL_BULK_SIG 0.001 Bulk signature with no Unsubscribe
HTML_IMAGE_ONLY_12 1.629 HTML: images with 800-1200 bytes of words
HTML_MESSAGE 0.001 HTML included in message
HTML_SHORT_LINK_IMG_1 0.139 HTML is very short with a linked image
KAM_DMARC_STATUS 0.01 Test Rule for DKIM or SPF Failure with Strict Alignment
KAM_EU 0.5 Prevalent use of .eu in spam/malware
KAM_GRABBAG2 5 Grabbag of Spams hitting EU domains and other indicators
KHOP_HELO_FCRDNS 0.4 Relay HELO differs from its IP's reverse DNS
MIME_HTML_ONLY 0.1 Message only has text/html MIME parts
MISSING_MID 0.14 Missing Message-Id: header
RAZOR2_CF_RANGE_51_100 2.43 Razor2 gives confidence level above 50%
RAZOR2_CHECK 1.729 Listed in Razor2 (http://razor.sf.net/)
SPF_HELO_NONE 0.001 SPF: HELO does not publish an SPF Record
T_KAM_HTML_FONT_INVALID 0.01 Test for Invalidly Named or Formatted Colors in HTML
T_REMOTE_IMAGE 0.01 Message contains an external image
URIBL_ABUSE_SURBL 1.948 Contains an URL listed in the ABUSE SURBL blocklist [telects.eu]
URIBL_BLACK 1.7 Contains an URL listed in the URIBL blacklist [telects.eu]
Rules attached, I believe I left those at the default values.
** after applying the rules as requested, continued to receive messages with that sender.
Header attached.
** received another this morning with FC7LX.R3OFC7LX@1JSV.brimmats.com when I test that in the regex it matches, but not sure yet since I havent been using PMG long the reason why it's not being rejected.
Todays header (AM):
Delivered-To: andrew@test.net
Return-Path:
Received: from email.seattle.gov (senke.deparench.eu [89.251.16.110])
by mgw.localdomain (Proxmox) with ESMTP id 37AEB809F1
for <andrew@test.net>; Mon, 12 Oct 2020 09:38:42 -0400 (EDT)
subject: SPAM: Say Bye To Moles And SkinTags
From: "DermaCorrect Skin Tags" <R3OFC7LX.R3OFC7LX@1JSV.brimmats.com>
To: alicia@web56.net
Content-Type: text/html; charset=utf-8;
Content-Disposition: inline
Date: Mon, 12 Oct 2020 09:00:48 -0400
X-SPAM-LEVEL: Spam detection results: 16
BODY_URI_ONLY 0.822 Message body is only a URI in one line of text or for an image
FSL_BULK_SIG 0.001 Bulk signature with no Unsubscribe
HTML_IMAGE_ONLY_12 1.629 HTML: images with 800-1200 bytes of words
HTML_MESSAGE 0.001 HTML included in message
HTML_SHORT_LINK_IMG_1 0.139 HTML is very short with a linked image
KAM_DMARC_STATUS 0.01 Test Rule for DKIM or SPF Failure with Strict Alignment
KAM_EU 0.5 Prevalent use of .eu in spam/malware
KAM_GRABBAG2 5 Grabbag of Spams hitting EU domains and other indicators
KHOP_HELO_FCRDNS 0.4 Relay HELO differs from its IP's reverse DNS
MIME_HTML_ONLY 0.1 Message only has text/html MIME parts
MISSING_MID 0.14 Missing Message-Id: header
RAZOR2_CF_RANGE_51_100 2.43 Razor2 gives confidence level above 50%
RAZOR2_CHECK 1.729 Listed in Razor2 (http://razor.sf.net/)
SPF_HELO_NONE 0.001 SPF: HELO does not publish an SPF Record
T_KAM_HTML_FONT_INVALID 0.01 Test for Invalidly Named or Formatted Colors in HTML
T_REMOTE_IMAGE 0.01 Message contains an external image
URIBL_ABUSE_SURBL 1.948 Contains an URL listed in the ABUSE SURBL blocklist [telects.eu]
URIBL_BLACK 1.7 Contains an URL listed in the URIBL blacklist [telects.eu]
Attachments
Last edited: