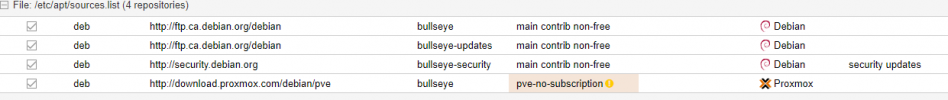
I've been using Proxmox for about 4 months now as a "non- enterprise" user (see screenshot below) and generally doing updates when they come up or soon after, which seems pretty frequently, IMO.
So far no issues but what's the risk to my operations of doing these updates in "production"? I'm using Proxmox to provide an internet firewall via Sophos UTM, and other services via Windows VM (UPS monitoring/control, internet reporting using Fastvue for Sophos, etc.). I have two remote installations and I don't want to cripple anything as I can't get there that quickly/easily and it is providing internet to multiple end users in both cases.
I don't have a lower state environment to test things in first. While this is for family (and I'm not making any money) so I do have some leeway if things go wrong, I don't have that much leeway given the somewhat critical need for internet access.
Bottom line, how often do updates in this category end up breaking things that were running fine before the update? Have the updates been thoroughly/widely tested before they are published? Is there a way I can manage the residual risk other than paying for a "lower state" environment? Worse case, is there a way I can roll back from an update, e.g. like Microsoft and Apple allow (even if only for a short time as is the case with Apple)?
Any info would be appreciated.
So far no issues but what's the risk to my operations of doing these updates in "production"? I'm using Proxmox to provide an internet firewall via Sophos UTM, and other services via Windows VM (UPS monitoring/control, internet reporting using Fastvue for Sophos, etc.). I have two remote installations and I don't want to cripple anything as I can't get there that quickly/easily and it is providing internet to multiple end users in both cases.
I don't have a lower state environment to test things in first. While this is for family (and I'm not making any money) so I do have some leeway if things go wrong, I don't have that much leeway given the somewhat critical need for internet access.

Bottom line, how often do updates in this category end up breaking things that were running fine before the update? Have the updates been thoroughly/widely tested before they are published? Is there a way I can manage the residual risk other than paying for a "lower state" environment? Worse case, is there a way I can roll back from an update, e.g. like Microsoft and Apple allow (even if only for a short time as is the case with Apple)?
Any info would be appreciated.

