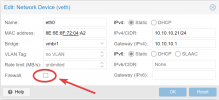
I have a proxmox server (soyoustart) with 2 bridges, one with public IPs (vmbr0) and another with a private network (vmbr1).
vmbr0 VMs work fine with public IPs, firewall on or firewall off
vmbr1 VMs or CTs only have internet if I disable the firewall check in the VM network device.
Anyone has had this problem? I need the VM or CT Firewall working even if they are in an internal network.
Host interfaces file:
vmbr0 VMs work fine with public IPs, firewall on or firewall off
vmbr1 VMs or CTs only have internet if I disable the firewall check in the VM network device.
Anyone has had this problem? I need the VM or CT Firewall working even if they are in an internal network.
Host interfaces file:
auto lo
iface lo inet loopback
auto eno3
iface eno3 inet static
address xxx.xx.18.14
netmask 255.255.255.255
pointopoint xxx.xx.18.254
gateway xxx.xx.18.254
hwaddress 0C:C4:7A:C3:52:A6
post-up echo 1 > /proc/sys/net/ipv4/conf/vmbr0/proxy_arp
iface eno4 inet manual
auto vmbr0
iface vmbr0 inet static
address xxx.xx.18.14
netmask 255.255.255.255
bridge-ports none
bridge-stp off
bridge-fd 0
up ip route add xxx.xxx.169.32/32 dev vmbr0
up ip route add xxx.xxx.169.33/32 dev vmbr0
up ip route add xxx.xxx.169.34/32 dev vmbr0
up ip route add xxx.xxx.169.35/32 dev vmbr0
up ip route add xxx.xxx.169.36/32 dev vmbr0
up ip route add xxx.xxx.169.37/32 dev vmbr0
up ip route add xxx.xxx.169.38/32 dev vmbr0
up ip route add xxx.xxx.169.39/32 dev vmbr0
up ip route add xxx.xxx.169.40/32 dev vmbr0
up ip route add xxx.xxx.169.41/32 dev vmbr0
up ip route add xxx.xxx.169.42/32 dev vmbr0
up ip route add xxx.xxx.169.43/32 dev vmbr0
up ip route add xxx.xxx.169.44/32 dev vmbr0
up ip route add xxx.xxx.169.45/32 dev vmbr0
up ip route add xxx.xxx.169.46/32 dev vmbr0
up ip route add xxx.xxx.169.47/32 dev vmbr0
auto vmbr1 # Second Bridge, internal network
iface vmbr1 inet static
address 10.10.10.1
netmask 255.255.255.0
bridge-ports none
bridge-stp off
bridge-fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '10.10.10.0/24' -o eno3 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '10.10.10.0/24' -o eno3 -j MASQUERADE