The new kernel 6.2 with some KVM improvements will be released on Sunday.
https://www.phoronix.com/news/Linux-6.2-KVM
I hope that will solve the problem.
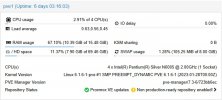
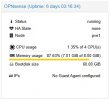
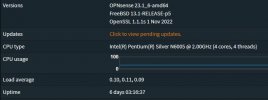
NAS motherboard N5105 (4x i226)
Proxmox 7.3-6
Kernel Linux 6.1.2-1-pve #1 SMP PREEMPT_DYNAMIC PVE 6.1.2-1
and activated c-state 1 in the bios.
Have 4 machines running Debian 11 and one running IPFire.
Last week an IPFire crash, the other machines have been running stably for weeks.
https://www.phoronix.com/news/Linux-6.2-KVM
I hope that will solve the problem.
NAS motherboard N5105 (4x i226)
Proxmox 7.3-6
Kernel Linux 6.1.2-1-pve #1 SMP PREEMPT_DYNAMIC PVE 6.1.2-1
and activated c-state 1 in the bios.
Have 4 machines running Debian 11 and one running IPFire.
Last week an IPFire crash, the other machines have been running stably for weeks.
Code:
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: KVM internal error. Suberror: 1
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: extra data[0]: 0x0000000000000001
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: extra data[1]: 0xe8ff6afcca010f0f
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: extra data[2]: 0x48c4894800000535
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: extra data[3]: 0x000000000000001e
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: extra data[4]: 0x0000000000000010
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: extra data[5]: 0x0000000000000000
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: extra data[6]: 0x0000000000000000
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: extra data[7]: 0x0000000000000000
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: emulation failure
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: RAX=ffffffffb067c560 RBX=ffffffffb1215940 RCX=0000000000000000 RDX=0000000000000000
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: RSI=0000000000000000 RDI=0000000000000000 RBP=0000000000000000 RSP=ffffffffb1203e68
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: R8 =0000000000000000 R9 =0000000000000000 R10=0000000000000000 R11=0000000000000000
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: R12=0000000000000000 R13=0000000000000000 R14=ffff96abffff7fc0 R15=ffffffffb1215118
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: RIP=ffffffffb0800df0 RFL=00000046 [---Z-P-] CPL=0 II=0 A20=1 SMM=0 HLT=0
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: ES =0000 0000000000000000 ffffffff 00c00000
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: CS =0010 0000000000000000 ffffffff 00a09b00 DPL=0 CS64 [-RA]
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: SS =0018 0000000000000000 ffffffff 00c09300 DPL=0 DS [-WA]
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: DS =0000 0000000000000000 ffffffff 00c00000
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: FS =0000 0000000000000000 ffffffff 00c00000
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: GS =0000 ffff96abf9c00000 ffffffff 00c00000
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: LDT=0000 0000000000000000 ffffffff 00c00000
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: TR =0040 fffffe0000003000 00004087 00008b00 DPL=0 TSS64-busy
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: GDT= fffffe0000001000 0000007f
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: IDT= fffffe0000000000 00000fff
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: CR0=80050033 CR2=000071a442e13008 CR3=0000000116138000 CR4=00350ef0
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: DR0=0000000000000000 DR1=0000000000000000 DR2=0000000000000000 DR3=0000000000000000
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: DR6=00000000ffff0ff0 DR7=0000000000000400
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: EFER=0000000000000d01
Feb 09 23:33:17 127.0.0.1 QEMU[1777]: Code=89 c4 48 89 e7 e8 5a 1a e7 ff e9 65 06 00 00 0f 1f 44 00 00 <0f> 01 ca fc 6a ff e8 35 05 00 00 48 89 c4 48 89 e7 e8 0a 19 e7 ff e9 45 06 00 00 0f 1f 44
Last edited: