Good morning, the firewall on a VM hasn't worked for me since yesterday. All the others work great. Naturally the firewall is enabled at all levels.... how can I fix it? I also checked that the VM's network card has the firewall flag active, I tried disabling and re-enabling it, I tried restarting the firewall services but nothing, all the other VMs work great, only this one gives me problems when up to it worked a few days ago. Thanks to anyone who can help me and sorry for the English but I'm translating with Google.
VM Firewall not working
- Thread starter mitroviqui
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Hello,
May you post the output of the `
May you post the output of the `
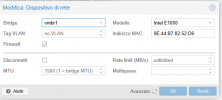
pve-firewall status` command? All other VMs are using the `Inet E1000` Model in their config?i ran a pve-firewall restart and now it tells me if I run pve-firewall status it tells me (pending changes), yes all VMs use net E1000
I noticed this in the PVE Syslog
Apr 20 14:57:57 Hypsrv-01 pve-firewall[287565]: status update error: iptables_restore_cmdlist: Try `iptables-restore -h' or 'iptables-restore --help' for more information.
Apr 20 14:57:57 Hypsrv-01 pve-firewall[287565]: status update error: iptables_restore_cmdlist: Try `iptables-restore -h' or 'iptables-restore --help' for more information.
I'm seeing a strange rule
with
64.0.0.0/8:164.0.0.0/8
(":" instead ",")
do you have create rule with gui ?
can you send content of /etc/pve/firewall/207.fw ?
Code:
-A tap207i0-IN -s 198.0.0.0/8,162.0.0.0/8,162.0.0.0/8,107.0.0.0/8,192.241.0.0/16,104.0.0.0/8,45.0.0.0/8,159.0.0.0/8,66.0.0.0/8,138.0.0.0/8,68.0.0.0/8,194.55.0.0/16,157.0.0.0/8,64.0.0.0/8:164.0.0.0/8,72.110.0.0/16 -p tcp -m limit --limit 1/sec -j NFLOG --nflog-prefix ":207:6:tap207i0-IN: REJECT: "with
64.0.0.0/8:164.0.0.0/8
(":" instead ",")
do you have create rule with gui ?
can you send content of /etc/pve/firewall/207.fw ?
Yes, with GUI...
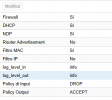
[OPTIONS]
log_level_in: nolog
enable: 1
ipfilter: 1
log_level_out: nolog
[RULES]
IN REJECT -i net0 -p icmp -log info
IN SMB(REJECT) -i net0 -source 192.168.1.15 -log info
IN SMB(ACCEPT) -i net0 -source 192.168.1.16-192.168.1.250 -log info
IN SMB(ACCEPT) -i net0 -source 192.168.1.3-192.168.1.14 -log info # SMB RETE INTERNA
IN REJECT -i net0 -source 192.241.0.0/16,179.43.0.0/16,79.110.0.0/16 -log info
IN REJECT -i net0 -source 162.0.0.0/8 -log info
IN REJECT -i net0 -source 107.0.0.0/8 -log info
IN REJECT -i net0 -source 198.0.0.0/8 -log info
IN REJECT -i net0 -source 198.0.0.0/8,162.0.0.0/8,162.0.0.0/8,107.0.0.0/8,192.241.0.0/16,104.0.0.0/8,45.0.0.0/8,159.0.0.0/8,66.0.0.0/8,138.0.0.0/8,68.0.0.0/8>
IN ACCEPT -i net0 -p tcp -dport 443 -log info # HTTPS
IN ACCEPT -i net0 -p tcp -dport 993 -log info # IMAPS
[OPTIONS]
log_level_in: nolog
enable: 1
ipfilter: 1
log_level_out: nolog
[RULES]
IN REJECT -i net0 -p icmp -log info
IN SMB(REJECT) -i net0 -source 192.168.1.15 -log info
IN SMB(ACCEPT) -i net0 -source 192.168.1.16-192.168.1.250 -log info
IN SMB(ACCEPT) -i net0 -source 192.168.1.3-192.168.1.14 -log info # SMB RETE INTERNA
IN REJECT -i net0 -source 192.241.0.0/16,179.43.0.0/16,79.110.0.0/16 -log info
IN REJECT -i net0 -source 162.0.0.0/8 -log info
IN REJECT -i net0 -source 107.0.0.0/8 -log info
IN REJECT -i net0 -source 198.0.0.0/8 -log info
IN REJECT -i net0 -source 198.0.0.0/8,162.0.0.0/8,162.0.0.0/8,107.0.0.0/8,192.241.0.0/16,104.0.0.0/8,45.0.0.0/8,159.0.0.0/8,66.0.0.0/8,138.0.0.0/8,68.0.0.0/8>
IN ACCEPT -i net0 -p tcp -dport 443 -log info # HTTPS
IN ACCEPT -i net0 -p tcp -dport 993 -log info # IMAPS
Is this long ip addresses string defined manually? Maybe it is alias?Yes, with GUI...
[OPTIONS]
log_level_in: nolog
enable: 1
ipfilter: 1
log_level_out: nolog
[RULES]
IN REJECT -i net0 -p icmp -log info
IN SMB(REJECT) -i net0 -source 192.168.1.15 -log info
IN SMB(ACCEPT) -i net0 -source 192.168.1.16-192.168.1.250 -log info
IN SMB(ACCEPT) -i net0 -source 192.168.1.3-192.168.1.14 -log info # SMB RETE INTERNA
IN REJECT -i net0 -source 192.241.0.0/16,179.43.0.0/16,79.110.0.0/16 -log info
IN REJECT -i net0 -source 162.0.0.0/8 -log info
IN REJECT -i net0 -source 107.0.0.0/8 -log info
IN REJECT -i net0 -source 198.0.0.0/8 -log info
IN REJECT -i net0 -source 198.0.0.0/8,162.0.0.0/8,162.0.0.0/8,107.0.0.0/8,192.241.0.0/16,104.0.0.0/8,45.0.0.0/8,159.0.0.0/8,66.0.0.0/8,138.0.0.0/8,68.0.0.0/8>
IN ACCEPT -i net0 -p tcp -dport 443 -log info # HTTPS
IN ACCEPT -i net0 -p tcp -dport 993 -log info # IMAPS
Yes, with GUI...
[OPTIONS]
log_level_in: nolog
enable: 1
ipfilter: 1
log_level_out: nolog
[RULES]
IN REJECT -i net0 -p icmp -log info
IN SMB(REJECT) -i net0 -source 192.168.1.15 -log info
IN SMB(ACCEPT) -i net0 -source 192.168.1.16-192.168.1.250 -log info
IN SMB(ACCEPT) -i net0 -source 192.168.1.3-192.168.1.14 -log info # SMB RETE INTERNA
IN REJECT -i net0 -source 192.241.0.0/16,179.43.0.0/16,79.110.0.0/16 -log info
IN REJECT -i net0 -source 162.0.0.0/8 -log info
IN REJECT -i net0 -source 107.0.0.0/8 -log info
IN REJECT -i net0 -source 198.0.0.0/8 -log info
IN REJECT -i net0 -source 198.0.0.0/8,162.0.0.0/8,162.0.0.0/8,107.0.0.0/8,192.241.0.0/16,104.0.0.0/8,45.0.0.0/8,159.0.0.0/8,66.0.0.0/8,138.0.0.0/8,68.0.0.0/8>
IN ACCEPT -i net0 -p tcp -dport 443 -log info # HTTPS
IN ACCEPT -i net0 -p tcp -dport 993 -log info # IMAPS
The ouput on the interesting long rule is truncated, can you resend with [\CODE] [\/CODE] ?
I think it's missing a check in the gui, because ':' shoudn't be allowed between 2 ips v4. (it's only valid for ipv6 address)
Last edited:
Manually...block External IPIs this long ip addresses string defined manually? Maybe it is alias?
WOW....deleting that rule everything started working again...THANK YOU!!!!! So I can't put too many IPs?
Try to use IPset, it very useful feature:WOW....deleting that rule everything started working again...THANK YOU!!!!! So I can't put too many IPs?
Datacenter -> Firewall -> IPSet
Then create firewall rule and choose IPSet you created in "Source" or "Destination" field, depend on your needs.
But you have to enter each ip/cdir manually.
Also, you may have individual IPSets for every VM (<VM> -> Firewall -> IPSet)
Last edited:
yes, you can. (but it's better to use ipset for performance)WOW....deleting that rule everything started working again...THANK YOU!!!!! So I can't put too many IPs?
the ":" is wrong . it should be ",".
This is a filtering bug in the gui.
(I have open a https://bugzilla.proxmox.com/show_bug.cgi?id=4685 for tracking)
Thanks, this solution solve for my issue. I had same issue, after check one by one vm firewall, there's strange config too