PVE 7.1-10
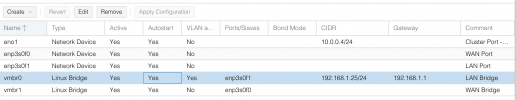
I had been successfully running a pfsense VM with VLAN tagging through the GUI/OVS for ~2 years prior to upgrading to PVE 7.x. Now, none of my tagged VM's can reach their gateways. VLAN routing is still working correctly in the rest of my network stack, it's only the VLAN Tagged VMs that have stuttered.
I have simplified the problem by using VLAN-aware Linux bridges, but this hasn't worked either. Even though it stopped working after the PVE upgrade, I considered that it might be a hardware issue with the NIC, so I installed a brand-new Intel NIC. Still nothing.
Here are what my logs look when I tag and untag a VM:
Tagging:
Untagging:
I'm not sure why we're seeing OVS errors in the logs since nobody in my cluster is on OVS at the moment.
Thank for the advice!
I had been successfully running a pfsense VM with VLAN tagging through the GUI/OVS for ~2 years prior to upgrading to PVE 7.x. Now, none of my tagged VM's can reach their gateways. VLAN routing is still working correctly in the rest of my network stack, it's only the VLAN Tagged VMs that have stuttered.
I have simplified the problem by using VLAN-aware Linux bridges, but this hasn't worked either. Even though it stopped working after the PVE upgrade, I considered that it might be a hardware issue with the NIC, so I installed a brand-new Intel NIC. Still nothing.


Here are what my logs look when I tag and untag a VM:
Tagging:
Code:
Jan 28 21:28:49 TracheNodeB pvedaemon[531415]: <root@pam> update VM 420: -net0 virtio=26:77:A8:6E:5E:4F,bridge=vmbr0,tag=3
Jan 28 21:28:49 TracheNodeB kernel: vmbr0: port 3(tap420i0) entered disabled state
Jan 28 21:28:49 TracheNodeB ovs-vsctl[3084464]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl del-port fwln420i0
Jan 28 21:28:49 TracheNodeB ovs-vsctl[3084464]: ovs|00002|db_ctl_base|ERR|no port named fwln420i0
Jan 28 21:28:49 TracheNodeB ovs-vsctl[3084465]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl del-port tap420i0
Jan 28 21:28:49 TracheNodeB ovs-vsctl[3084465]: ovs|00002|db_ctl_base|ERR|no port named tap420i0
Jan 28 21:28:49 TracheNodeB ovs-vsctl[3084466]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl del-port tap420i0
Jan 28 21:28:49 TracheNodeB ovs-vsctl[3084466]: ovs|00002|db_ctl_base|ERR|no port named tap420i0
Jan 28 21:28:49 TracheNodeB ovs-vsctl[3084467]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl del-port fwln420i0
Jan 28 21:28:49 TracheNodeB ovs-vsctl[3084467]: ovs|00002|db_ctl_base|ERR|no port named fwln420i0
Jan 28 21:28:49 TracheNodeB kernel: vmbr0: port 3(tap420i0) entered blocking state
Jan 28 21:28:49 TracheNodeB kernel: vmbr0: port 3(tap420i0) entered disabled state
Jan 28 21:28:49 TracheNodeB kernel: vmbr0: port 3(tap420i0) entered blocking state
Jan 28 21:28:49 TracheNodeB kernel: vmbr0: port 3(tap420i0) entered forwarding state
Jan 28 21:29:42 TracheNodeB pmxcfs[1952]: [dcdb] notice: data verification successfulUntagging:
Code:
Jan 28 21:29:50 TracheNodeB pvedaemon[531417]: <root@pam> update VM 420: -net0 virtio=26:77:A8:6E:5E:4F,bridge=vmbr0
Jan 28 21:29:50 TracheNodeB kernel: vmbr0: port 3(tap420i0) entered disabled state
Jan 28 21:29:50 TracheNodeB ovs-vsctl[3086020]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl del-port fwln420i0
Jan 28 21:29:50 TracheNodeB ovs-vsctl[3086020]: ovs|00002|db_ctl_base|ERR|no port named fwln420i0
Jan 28 21:29:50 TracheNodeB ovs-vsctl[3086021]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl del-port tap420i0
Jan 28 21:29:50 TracheNodeB ovs-vsctl[3086021]: ovs|00002|db_ctl_base|ERR|no port named tap420i0
Jan 28 21:29:50 TracheNodeB ovs-vsctl[3086022]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl del-port tap420i0
Jan 28 21:29:50 TracheNodeB ovs-vsctl[3086022]: ovs|00002|db_ctl_base|ERR|no port named tap420i0
Jan 28 21:29:50 TracheNodeB ovs-vsctl[3086023]: ovs|00001|vsctl|INFO|Called as /usr/bin/ovs-vsctl del-port fwln420i0
Jan 28 21:29:50 TracheNodeB ovs-vsctl[3086023]: ovs|00002|db_ctl_base|ERR|no port named fwln420i0
Jan 28 21:29:50 TracheNodeB kernel: vmbr0: port 3(tap420i0) entered blocking state
Jan 28 21:29:50 TracheNodeB kernel: vmbr0: port 3(tap420i0) entered disabled state
Jan 28 21:29:50 TracheNodeB kernel: vmbr0: port 3(tap420i0) entered blocking state
Jan 28 21:29:50 TracheNodeB kernel: vmbr0: port 3(tap420i0) entered forwarding stateI'm not sure why we're seeing OVS errors in the logs since nobody in my cluster is on OVS at the moment.
Thank for the advice!

