Hi, I was wondering if someone else has accomplish this. Not sure why im struggling, I have done it before when pfSense was on bare metal but no sure whats the issue.
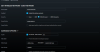
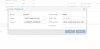
Currently pfSense is virtualized inside of Proxmox 5.0. Which is connected to a netgear smart switch which i configured the tag ports 2 and 4 (p2 is proxmox and p4 is unifi ap). And the AP unifi created another guest network with vlan 50 see picture.
I was looking around saw few users saying to connect a linux bridge or bond but not sure.
Thank you
Currently pfSense is virtualized inside of Proxmox 5.0. Which is connected to a netgear smart switch which i configured the tag ports 2 and 4 (p2 is proxmox and p4 is unifi ap). And the AP unifi created another guest network with vlan 50 see picture.
I was looking around saw few users saying to connect a linux bridge or bond but not sure.
Thank you