Hi
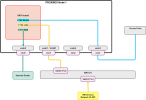
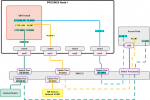
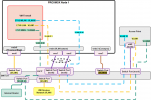
I'm relatively new to networking with VLANs, so I hope this isn't a dumb question.. I have a proxmox host with 4 nics. 1 goes to the modem, 3 others are connected to a vlan-aware Linux Bridge. A pfSense VM is connecting WAN and LAN. 1 of those internal NICs is connected to a trunk port of my Zyxel managed switch. Another internal NIC goes to a wifi accespoint. Other ports on the switch are all acces ports for VLAN1 and devices attached to it have functional internet connections. Now, I wanted to add a separate wifi network for untrusted devices. As a first step, I added it with VLAN enabled and set to VLAN1. I had expected this to work the same as the untagged wifi networks because (I assume) the primare VLAN id for the linux bridge is 1, but it isn't. I do not get an IP if I try to connect to this SSID. What am I doing wrong here, or what have I failed to understand about VLANs?
Kind regards,
Merijn
I'm relatively new to networking with VLANs, so I hope this isn't a dumb question.. I have a proxmox host with 4 nics. 1 goes to the modem, 3 others are connected to a vlan-aware Linux Bridge. A pfSense VM is connecting WAN and LAN. 1 of those internal NICs is connected to a trunk port of my Zyxel managed switch. Another internal NIC goes to a wifi accespoint. Other ports on the switch are all acces ports for VLAN1 and devices attached to it have functional internet connections. Now, I wanted to add a separate wifi network for untrusted devices. As a first step, I added it with VLAN enabled and set to VLAN1. I had expected this to work the same as the untagged wifi networks because (I assume) the primare VLAN id for the linux bridge is 1, but it isn't. I do not get an IP if I try to connect to this SSID. What am I doing wrong here, or what have I failed to understand about VLANs?
Kind regards,
Merijn