Situation:
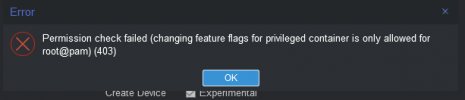
Is this by design? - in need of explanation here ...
.. i mean i explicitly went for a federative method so i have control on authentication and give correct permissions/authorisations this way on a corporate level, but even then i am still dependant on root@pam for some tasks.
- Glowsome
- OIDC correctly setup
- OIDC user is part of Administrators - group, with the correct rights.
- change LXC options ( ie. nesting/Fuse tick if unticked)

Is this by design? - in need of explanation here ...
.. i mean i explicitly went for a federative method so i have control on authentication and give correct permissions/authorisations this way on a corporate level, but even then i am still dependant on root@pam for some tasks.
- Glowsome

