New to networking practice i have a case i want to implement to have the most security and to exercice a bit.
I have a nginx server i want to be public and receive communications to route to my dev services (jenkins in this example), i wanted to make the nginx be able to contact public thats why its using the vmbr0 passing through my home network subnet.
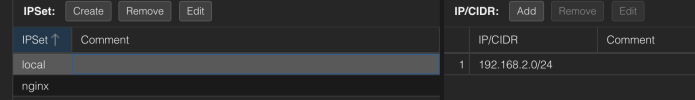
I have the other vmbr1 which only contains communications between my containers on another subnet than my home network in this case 192.168.3.0/24. Is it possible to make the vmbr0 have public access without being able to contact my other home network(i know that it passes through my home subnet so might no be possible).
Is it a good idea to put all these services on the same subnet as my home network and put those in a dmz in my router? (the router only can add ips to the dmz from the same home subnet 192.168.2.0/24). Sorry if this might sound stupid but just trying to make it make sense, i might be creating problems that dont exist or not possible. the ultimate goal is setup the most secure way for me to have a standalone network for the vms i want public for my web services without inducing risk on my home network. I don't have the ability to create vlans in my router or add other ips outside my subnet in the dmz.
For your info i created a nginx in aws ec2 cause i heard it's always good practice to have the reverse proxy outside your local network, so the one i have locally might be useless in my case, enlighten me if possible.
thanks yall!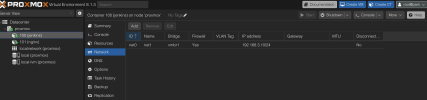
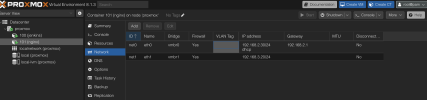
I have a nginx server i want to be public and receive communications to route to my dev services (jenkins in this example), i wanted to make the nginx be able to contact public thats why its using the vmbr0 passing through my home network subnet.
I have the other vmbr1 which only contains communications between my containers on another subnet than my home network in this case 192.168.3.0/24. Is it possible to make the vmbr0 have public access without being able to contact my other home network(i know that it passes through my home subnet so might no be possible).
Is it a good idea to put all these services on the same subnet as my home network and put those in a dmz in my router? (the router only can add ips to the dmz from the same home subnet 192.168.2.0/24). Sorry if this might sound stupid but just trying to make it make sense, i might be creating problems that dont exist or not possible. the ultimate goal is setup the most secure way for me to have a standalone network for the vms i want public for my web services without inducing risk on my home network. I don't have the ability to create vlans in my router or add other ips outside my subnet in the dmz.
For your info i created a nginx in aws ec2 cause i heard it's always good practice to have the reverse proxy outside your local network, so the one i have locally might be useless in my case, enlighten me if possible.
thanks yall!




Last edited:

