Hello Guys,
I am really scratching my head trying to passthrough an usb device to a Windows10 vm.
The device is a "Gemalto SafeNet eToken" containing a certificate for e-signing.
The device has been detected and was appearing at "lsusb", also I have configured:
- did not enabled "iommu=pt" yet
After hypervisor reboot we can see:
I have also did, although I am NOT sure was necessarily, especially regarding "vfio_pci" :
Therefore we have,
lsmod | grep vfio
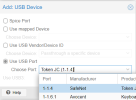
Then, I've added the USB device to the vm from the UI as "Use USB Vendor/Device ID" -> selected the SafeNet device -> power up the vm
Neither the above or "qm set 101 -usb0 host=0529:0620" made the token appear inside the vm.
The hypervisor is a Dell PowerEdge R720 and the bios has already the "Virtualisation Technology" enabled. But SRV-IOV not.
I just dont understand where I did wrong, or anything more is needed to be configured.
Please let me know if any thoughts of misconfigurations that you may notice withing the above. Also I am not sure if I need to blacklist this device as well.
Thank you so much !
Leo
I am really scratching my head trying to passthrough an usb device to a Windows10 vm.
The device is a "Gemalto SafeNet eToken" containing a certificate for e-signing.
The device has been detected and was appearing at "lsusb", also I have configured:
Code:
cat /etc/default/grub | grep GRUB_CMDLINE_LINUX_DEFAULT
GRUB_CMDLINE_LINUX_DEFAULT="quiet intel_iommu=on"
Code:
cat /proc/cmdline
BOOT_IMAGE=/boot/vmlinuz-6.2.16-15-pve root=/dev/mapper/pve-root ro quiet intel_iommu=onAfter hypervisor reboot we can see:
Code:
dmesg | grep -e DMAR -e IOMMU -e AMD-Vi
[ 0.014874] ACPI: DMAR 0x00000000CD3346F4 000158 (v01 DELL PE_SC3 00000001 DELL 00000001)
[ 0.014934] ACPI: Reserving DMAR table memory at [mem 0xcd3346f4-0xcd33484b]
[ 0.826804] DMAR: IOMMU enabled
[ 2.068951] DMAR: Host address width 46
[ 2.068953] DMAR: DRHD base: 0x000000d5000000 flags: 0x0
[ 2.068961] DMAR: dmar0: reg_base_addr d5000000 ver 1:0 cap d2078c106f0462 ecap f020fe
[ 2.068964] DMAR: DRHD base: 0x000000de900000 flags: 0x1
[ 2.068970] DMAR: dmar1: reg_base_addr de900000 ver 1:0 cap d2078c106f0462 ecap f020fe
[ 2.068973] DMAR: RMRR base: 0x000000cf458000 end: 0x000000cf46ffff
[ 2.068975] DMAR: RMRR base: 0x000000cf450000 end: 0x000000cf450fff
[ 2.068977] DMAR: RMRR base: 0x000000cf452000 end: 0x000000cf452fff
[ 2.068978] DMAR: ATSR flags: 0x0
[ 2.068982] DMAR-IR: IOAPIC id 2 under DRHD base 0xd5000000 IOMMU 0
[ 2.068984] DMAR-IR: IOAPIC id 0 under DRHD base 0xde900000 IOMMU 1
[ 2.068986] DMAR-IR: IOAPIC id 1 under DRHD base 0xde900000 IOMMU 1
[ 2.068987] DMAR-IR: HPET id 0 under DRHD base 0xde900000
[ 2.068989] DMAR-IR: x2apic is disabled because BIOS sets x2apic opt out bit.
[ 2.068990] DMAR-IR: Use 'intremap=no_x2apic_optout' to override the BIOS setting.
[ 2.069631] DMAR-IR: Enabled IRQ remapping in xapic mode
[ 4.770440] DMAR: No SATC found
[ 4.770444] DMAR: dmar0: Using Queued invalidation
[ 4.770452] DMAR: dmar1: Using Queued invalidation
[ 4.814048] DMAR: Intel(R) Virtualization Technology for Directed I/O
[10690.806273] DMAR: DRHD: handling fault status reg 2
[10690.806330] DMAR: [DMA Read NO_PASID] Request device [00:1a.0] fault addr 0xe8000 [fault reason 0x06] PTE Read access is not setI have also did, although I am NOT sure was necessarily, especially regarding "vfio_pci" :
Code:
modprobe vfio
modprobe vfio_iommu_type1
modprobe vfio_pciTherefore we have,
lsmod | grep vfio
Code:
vfio_pci 16384 0
vfio_pci_core 94208 1 vfio_pci
vfio_iommu_type1 49152 0
vfio 57344 3 vfio_pci_core,vfio_iommu_type1,vfio_pci
iommufd 73728 1 vfio
irqbypass 16384 80 vfio_pci_core,kvmThen, I've added the USB device to the vm from the UI as "Use USB Vendor/Device ID" -> selected the SafeNet device -> power up the vm
Neither the above or "qm set 101 -usb0 host=0529:0620" made the token appear inside the vm.
Code:
pveversion
pve-manager/8.0.4/d258a813cfa6b390 (running kernel: 6.2.16-15-pve)The hypervisor is a Dell PowerEdge R720 and the bios has already the "Virtualisation Technology" enabled. But SRV-IOV not.
I just dont understand where I did wrong, or anything more is needed to be configured.
Please let me know if any thoughts of misconfigurations that you may notice withing the above. Also I am not sure if I need to blacklist this device as well.
Thank you so much !
Leo