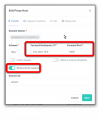
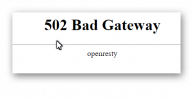
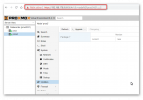
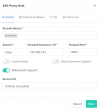
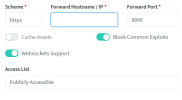
I have an nginx reverse proxy running in an unprivileged container to access resources running in other containers / VM's with my 1 public IP. My nginx configuration is listed below. I can access the web interface, but I can't access the console on any of my VM's, containers, or host. I'm assuming this has to do with the reverse proxy configuration and VNC ports, but I'm unsure what port mapping I need to modify to make this work. I'd think that this is a pretty common setup.
(server and server_name are modified because the forum won't let me post 'links')
(server and server_name are modified because the forum won't let me post 'links')
Code:
upstream pvehost {
server 10.3.2.100:8006;
}
server {
listen 80 http2;
listen [::]:80 http2;
server_name sub.domain.com;
return 301 htt ps://$server_name$request_uri;
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
server_name sub.domain.com;
ssl_certificate /etc/letsencrypt/certs/star_domain_me/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/certs/star_domain_me/privkey.pem;
location / {
proxy_pass htt ps://pvehost;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_http_version 1.1;
}
}