Looks like I am trying to create a similar setup many before have successfully implemented and I am only adding to the pool of confused admins...
I am trying to trunk several VLANs to a pfSense VM over a physical interface (eno3). Here I the steps:
Here is the relevant sections of my /etc/network/interfaces:
Is there anything else I can provide to help us troubleshoot this?
I am trying to trunk several VLANs to a pfSense VM over a physical interface (eno3). Here I the steps:
- Configure Trunking on switch (Cisco Catalyst 3560) without a native VLAN (I don't need anything untagged)
Code:interface GigabitEthernet0/3 switchport trunk encapsulation dot1q switchport trunk allowed vlan 100,300,400 switchport mode trunk ! - Plug Proxmox interface eno3 into port 0/3
- Create a bridge
- Name: vmbr2
- autostart: checked
- VLAN aware: checked
- Bridge port: eno3
- Create VLAN 100
- Name: vmbr2.100
- IPv4/CIDR: 10.1.0.98/24
- autostart: checked
- Vlan raw device: vmbr2
- VLAN tag: 100
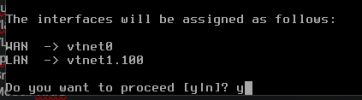
- On my pfSense VM, I create a NIC (vtnet1)
- Bridge: vmbr2
- Model: VirtIO
- VLAN Tag: 100
- Firewall: checked and unchecked (both not working)
- In pfSense I do the following:
Here is the relevant sections of my /etc/network/interfaces:
Code:
auto eno3
iface eno3 inet manual
auto vmbr2
iface vmbr2 inet manual
bridge-ports eno3
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
#Server traffic bridge
auto vmbr2.100
iface vmbr2.100 inet static
address 10.1.0.98/24
#VLAN 100Is there anything else I can provide to help us troubleshoot this?