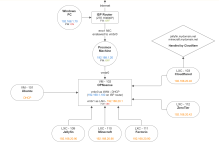
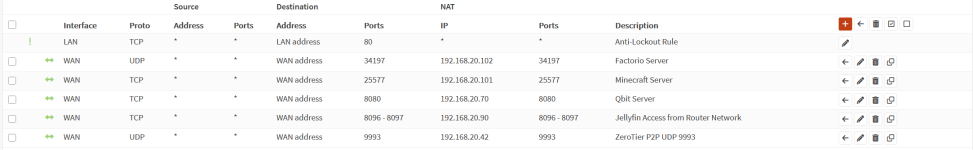
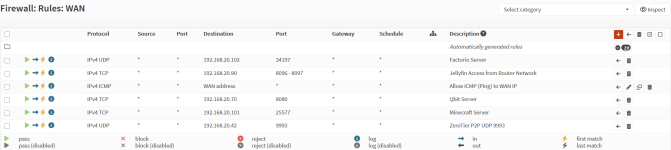
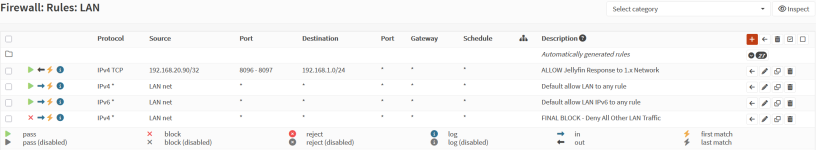
10:24:02.004820 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 36764:37001, ack 1, win 594, length 237
10:24:02.059400 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 37001, win 4104, length 0
10:24:02.103580 IP 198.41.200.63.7844 > 192.168.1.100.27366: UDP, length 21
10:24:02.108868 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 37001:37315, ack 1, win 594, length 314
10:24:02.127163 IP 192.168.1.100.48098 > 198.41.200.193.7844: UDP, length 41
10:24:02.129296 IP 192.168.1.100.27366 > 198.41.200.63.7844: UDP, length 49
10:24:02.152473 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 37315, win 4103, length 0
10:24:02.168324 IP 198.41.200.193.7844 > 192.168.1.100.48098: UDP, length 32
10:24:02.212780 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 37315:37785, ack 1, win 594, length 470
10:24:02.261062 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 37785, win 4101, length 0
10:24:02.316783 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 37785:38022, ack 1, win 594, length 237
10:24:02.317108 IP 192.168.1.100.44841 > 198.41.192.77.7844: UDP, length 41
10:24:02.369614 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 38022, win 4106, length 0
10:24:02.398423 IP 198.41.192.77.7844 > 192.168.1.100.44841: UDP, length 29
10:24:02.420866 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 38022:38413, ack 1, win 594, length 391
10:24:02.455450 IP 192.168.1.70.52089 > 192.168.1.100.8096: Flags [S], seq 3172986105, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
10:24:02.455718 IP 192.168.1.100.8096 > 192.168.1.70.52089: Flags [S.], seq 3895099770, ack 3172986106, win 64240, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
10:24:02.456264 IP 192.168.1.1 > 192.168.1.100: ICMP redirect 192.168.1.70 to host 192.168.1.70, length 60
10:24:02.456944 IP 192.168.1.70.52089 > 192.168.1.100.8096: Flags [.], ack 1, win 513, length 0
10:24:02.457047 IP 192.168.1.70.52089 > 192.168.1.100.8096: Flags [P.], seq 1:412, ack 1, win 513, length 411
10:24:02.457421 IP 192.168.1.100.8096 > 192.168.1.70.52089: Flags [.], ack 412, win 501, length 0
10:24:02.457454 IP 192.168.1.100.8096 > 192.168.1.70.52089: Flags [P.], seq 1:112, ack 412, win 501, length 111
10:24:02.462648 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 38413, win 4104, length 0
10:24:02.524868 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 38413:39507, ack 1, win 594, length 1094
10:24:02.535958 ARP, Request who-has 192.168.1.106 tell 192.168.1.115, length 46
10:24:02.537111 ARP, Request who-has 192.168.1.110 tell 192.168.1.115, length 46
10:24:02.538275 ARP, Request who-has 192.168.1.1 tell 192.168.1.115, length 46
10:24:02.539486 ARP, Request who-has 192.168.1.104 tell 192.168.1.115, length 46
10:24:02.549043 IP 192.168.1.100.42923 > one.one.one.one.domain: 22651+ PTR? 1.20.168.192.in-addr.arpa. (43)
10:24:02.566643 IP one.one.one.one.domain > 192.168.1.100.42923: 22651 NXDomain 0/0/0 (43)
10:24:02.567032 IP 192.168.1.100.61336 > one.one.one.one.domain: 41801+ PTR? 70.1.168.192.in-addr.arpa. (43)
10:24:02.567274 IP pve.local.8006 > 192.168.1.70.52036: Flags [P.], seq 3313457397:3313457756, ack 1271465990, win 594, length 359
10:24:02.571340 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 39507, win 4106, length 0
10:24:02.584682 IP one.one.one.one.domain > 192.168.1.100.61336: 41801 NXDomain 0/0/0 (43)
10:24:02.585321 IP pve.local.8006 > 192.168.1.70.52036: Flags [P.], seq 359:924, ack 1, win 594, length 565
10:24:02.585544 IP 192.168.1.70.52036 > pve.local.8006: Flags [.], ack 924, win 4106, length 0
10:24:02.628753 IP pve.local.50390 > one.one.one.one.domain: 47818+ PTR? 106.1.168.192.in-addr.arpa. (44)
10:24:02.628920 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 39507:39645, ack 1, win 594, length 138
10:24:02.646152 IP one.one.one.one.domain > pve.local.50390: 47818 NXDomain 0/0/0 (44)
10:24:02.646449 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 39645:40836, ack 1, win 594, length 1191
10:24:02.646800 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 40836, win 4101, length 0
10:24:02.653867 IP 192.168.1.100.2288 > one.one.one.one.domain: 55584+ PTR? 1.1.1.1.in-addr.arpa. (38)
10:24:02.660758 IP 192.168.1.100.8096 > 192.168.1.70.52089: Flags [P.], seq 1:112, ack 412, win 501, length 111
10:24:02.671132 IP one.one.one.one.domain > 192.168.1.100.2288: 55584 1/0/0 PTR one.one.one.one. (67)
10:24:02.671753 IP pve.local.8006 > 192.168.1.70.52036: Flags [P.], seq 924:1362, ack 1, win 594, length 438
10:24:02.695770 IP 198.41.192.67.7844 > 192.168.1.100.21210: UDP, length 21
10:24:02.721330 IP 192.168.1.100.21210 > 198.41.192.67.7844: UDP, length 60
10:24:02.726438 IP 192.168.1.70.52036 > pve.local.8006: Flags [.], ack 1362, win 4104, length 0
10:24:02.732916 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 40836:42063, ack 1, win 594, length 1227
10:24:02.756990 IP pve.local.8006 > 192.168.1.70.52036: Flags [P.], seq 1362:1716, ack 1, win 594, length 354
10:24:02.757566 IP 192.168.1.70.52089 > 192.168.1.100.8096: Flags [P.], seq 1:412, ack 1, win 513, length 411
10:24:02.757847 IP 192.168.1.100.8096 > 192.168.1.70.52089: Flags [.], ack 412, win 501, options [nop,nop,sack 1 {1:412}], length 0
10:24:02.788548 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 42063, win 4106, length 0
10:24:02.804059 IP 192.168.1.70.52036 > pve.local.8006: Flags [.], ack 1716, win 4103, length 0
10:24:02.836815 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 42063:42753, ack 1, win 594, length 690
10:24:02.861060 IP pve.local.8006 > 192.168.1.70.52036: Flags [P.], seq 1716:1990, ack 1, win 594, length 274
10:24:02.868765 IP 192.168.1.100.8096 > 192.168.1.70.52089: Flags [P.], seq 1:112, ack 412, win 501, length 111
10:24:02.881526 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 42753, win 4103, length 0
10:24:02.912577 IP 192.168.1.70.52036 > pve.local.8006: Flags [.], ack 1990, win 4102, length 0
10:24:02.940850 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 42753:43311, ack 1, win 594, length 558
10:24:02.965022 IP pve.local.8006 > 192.168.1.70.52036: Flags [P.], seq 1990:2129, ack 1, win 594, length 139
10:24:02.990207 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 43311, win 4101, length 0
...
10:24:08.036824 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 69533:69771, ack 30, win 594, length 238
10:24:08.078591 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 69771, win 4102, length 0
10:24:08.140883 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 69771:70009, ack 30, win 594, length 238
10:24:08.155484 IP 198.41.200.63.7844 > 192.168.1.100.27366: UDP, length 21
10:24:08.178222 IP 192.168.1.100.48098 > 198.41.200.193.7844: UDP, length 41
10:24:08.181423 IP 192.168.1.100.27366 > 198.41.200.63.7844: UDP, length 49
10:24:08.187174 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 70009, win 4101, length 0
10:24:08.219357 IP 198.41.200.193.7844 > 192.168.1.100.48098: UDP, length 32
10:24:08.244921 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 70009:70557, ack 30, win 594, length 548
10:24:08.295784 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 70557, win 4106, length 0
10:24:08.348865 IP pve.local.8006 > 192.168.1.70.52026: Flags [P.], seq 70557:70795, ack 30, win 594, length 238
10:24:08.358153 ARP, Request who-has 192.168.1.100 (bc:24:11:94:3f:c9 (oui Unknown)) tell 192.168.1.70, length 46
10:24:08.358317 ARP, Reply 192.168.1.100 is-at bc:24:11:94:3f:c9 (oui Unknown), length 28
10:24:08.388862 IP 192.168.1.70.52026 > pve.local.8006: Flags [.], ack 70795, win 4105, length 0
10:24:08.428689 IP 192.168.1.70.52098 > pve.local.8006: Flags [S], seq 3521541508, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
10:24:08.428707 IP pve.local.8006 > 192.168.1.70.52098: Flags [S.], seq 1134567808, ack 3521541509, win 64240, options [mss 1460,nop,nop,sackOK,nop,wscale 7], length 0
10:24:08.429519 IP 192.168.1.70.52098 > pve.local.8006: Flags [.], ack 1, win 4106, length 0
10:24:08.429966 IP 192.168.1.70.52098 > pve.local.8006: Flags [.], seq 1:1461, ack 1, win 4106, length 1460
10:24:08.429974 IP pve.local.8006 > 192.168.1.70.52098: Flags [.], ack 1461, win 525, length 0
10:24:08.430079 IP 192.168.1.70.52098 > pve.local.8006: Flags [P.], seq 1461:2400, ack 1, win 4106, length 939
10:24:08.430085 IP pve.local.8006 > 192.168.1.70.52098: Flags [.], ack 2400, win 548, length 0
10:24:08.431869 IP pve.local.8006 > 192.168.1.70.52098: Flags [P.], seq 1:2911, ack 2400, win 548, length 2910
10:24:08.432848 IP 192.168.1.70.52098 > pve.local.8006: Flags [.], ack 2911, win 4106, length 0
10:24:08.433566 IP 192.168.1.70.52098 > pve.local.8006: Flags [P.], seq 2400:2480, ack 2911, win 4106, length 80
10:24:08.433676 IP 192.168.1.70.52098 > pve.local.8006: Flags [P.], seq 2480:3417, ack 2911, win 4106, length 937
10:24:08.433776 IP pve.local.8006 > 192.168.1.70.52098: Flags [P.], seq 2911:3421, ack 3417, win 571, length 510
10:24:08.435295 IP pve.local.8006 > 192.168.1.70.52098: Flags [P.], seq 3421:4629, ack 3417, win 571, length 1208
10:24:08.435512 IP 192.168.1.70.52098 > pve.local.8006: Flags [.], ack 4629, win 4106, length 0
10:24:08.444059 IP 192.168.1.70.52098 > pve.local.8006: Flags [P.], seq 3417:4358, ack 4629, win 4106, length 941
10:24:08.446999 IP pve.local.8006 > 192.168.1.70.52098: Flags [P.], seq 4629:6123, ack 4358, win 594, length 1494
10:24:08.447265 IP 192.168.1.70.52098 > pve.local.8006: Flags [.], ack 6123, win 4106, length 0