Hello,
we set up OpenID Connect on our PVE 7.4 Cluster, authenticating against AzureAD.
When selecting the OIDC-realm for login, PVE does correctly redirect to the Microsoft-Login. However, after logging in on AzureAD and being redirected back to PVE, PVE just shows a busy pointer and after a while a timeout error appears:
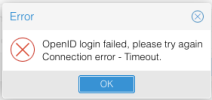
We have been suspecting an issue with the local user name not matching whatever is returned via OIDC. So we tried all possible username claims and changing the scopes, but at best still had the timeout - at worst received an error about scopes not being available at all.
We also tried not creating the user manually and instead set the Autocreate Users option, to see how PVE would spell out the user names. This still ended in a timeout - and no user was created in PVE at all.
The AzureAD ist not under our own administration, so our diagnosing on that end is very limited. Their support has not been able to find anything resolving the problem.
Can you help us with diagnosing and fixing this timeout issue? At the moment, we are out of ideas where to even look.
regards,
Andreas
P.S.: We also checked that the (manually created) local user supposed to match had Audit permissions, so the login doesn't just fail due to not being able to access PVE. Didn't help either, though.
we set up OpenID Connect on our PVE 7.4 Cluster, authenticating against AzureAD.
When selecting the OIDC-realm for login, PVE does correctly redirect to the Microsoft-Login. However, after logging in on AzureAD and being redirected back to PVE, PVE just shows a busy pointer and after a while a timeout error appears:

We have been suspecting an issue with the local user name not matching whatever is returned via OIDC. So we tried all possible username claims and changing the scopes, but at best still had the timeout - at worst received an error about scopes not being available at all.
We also tried not creating the user manually and instead set the Autocreate Users option, to see how PVE would spell out the user names. This still ended in a timeout - and no user was created in PVE at all.
The AzureAD ist not under our own administration, so our diagnosing on that end is very limited. Their support has not been able to find anything resolving the problem.
Can you help us with diagnosing and fixing this timeout issue? At the moment, we are out of ideas where to even look.
regards,
Andreas
P.S.: We also checked that the (manually created) local user supposed to match had Audit permissions, so the login doesn't just fail due to not being able to access PVE. Didn't help either, though.
Last edited:

