THank you in advace for anyone helping.
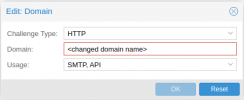
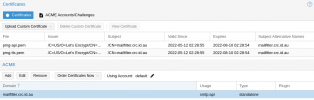
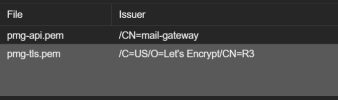
I have configured PMG 6.3-5 and updated the file:
This is working properly for the GUI and passes. All email flows correctly unsecured.
However when I try to connect on Thunderbird ports 25/26 with TLS - it says it has self-signed certificate when connecting.
I used NetCat and 250-STARTTLS is showing on both ports:
I have rebooted the server - how can I correctly update the SSL for these connections?
I have configured PMG 6.3-5 and updated the file:
/etc/pmg/pmg-api.pemThis is working properly for the GUI and passes. All email flows correctly unsecured.
However when I try to connect on Thunderbird ports 25/26 with TLS - it says it has self-signed certificate when connecting.
I used NetCat and 250-STARTTLS is showing on both ports:
Code:
admin@splaam:~$ nc -v localhost 26
DNS fwd/rev mismatch: localhost.domain.com.au != ip6-localhost
localhost.domain.com.au [127.0.0.1] 26 (?) open
220 splaam.domain.com.au Mail Gateway
ehlo test.com
250-splaam.domain.com.au
250-PIPELINING
250-SIZE 52430000
250-VRFY
250-ETRN
250-STARTTLS
250-ENHANCEDSTATUSCODES
250-8BITMIME
250-DSN
250-SMTPUTF8
250 CHUNKINGI have rebooted the server - how can I correctly update the SSL for these connections?
Last edited: