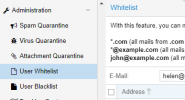
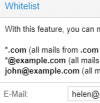
I have been advised of the following SPAM:
HEADER
SIMPLIFIED HEADER
SYSLOG
The above shows that it has gone through the PMG spam.DOMAIN.com.au .. It shows in the SYSLOGS but does not show in the Tracking Centre.
It is clearly SPAM, but somehow it is allowed through?
The recipient does not have any whitelist. I have not stipulated any IP/DNS whitelisting for this origin in the custom.cf file or via GUI.
PMG is 7.3-3 (just updated to 7.3-4 just before I made this post).
Anyone recommend what actions I should consider?
HEADER
Code:
Received: from SERVER.internal.local (192.168.000.000) by SERVER.internal.local
(192.168.000.000) with Microsoft SMTP Server (version=TLS1_2,
cipher=TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384) id 15.1.2507.21 via
Mailbox Transport; Sat, 17 Jun 2023 06:50:43 +1000
Received: from SERVER.internal.local (192.168.000.000) by SERVER.internal.local
(192.168.000.000) with Microsoft SMTP Server (version=TLS1_2,
cipher=TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384) id 15.1.2507.21; Sat, 17
Jun 2023 06:50:43 +1000
Received: from spam.DOMAIN.com.au (192.168.18.17) by SERVER.internal.local
(192.168.000.000) with Microsoft SMTP Server (version=TLS1_2,
cipher=TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384) id 15.1.2507.21 via
Frontend Transport; Sat, 17 Jun 2023 06:50:43 +1000
Received: from spam.DOMAIN.com.au (localhost.localdomain [127.0.0.1])
by spam.DOMAIN.com.au (Proxmox) with ESMTP id 41B16180BCE
for <helen@RECIPIENT.com.au>; Sat, 17 Jun 2023 06:50:43 +1000 (AEST)
Received: from mail2.payonline.ru (mail.payonline.ru [91.205.9.213])
(using TLSv1 with cipher ECDHE-RSA-AES256-SHA (256/256 bits))
(No client certificate requested)
by spam.DOMAIN.com.au (Proxmox) with ESMTPS id 29FCA180B24
for <helen@RECIPIENT.com.au>; Sat, 17 Jun 2023 06:50:39 +1000 (AEST)
Received: from User (45.88.66.146) by MAIL2.payonline.space (192.168.10.32)
with Microsoft SMTP Server (TLS) id 15.0.847.32; Thu, 15 Jun 2023 13:37:15
+0300
Reply-To: <www.imf2017@gmail.com>
From: <GLEN@spam.DOMAIN.com.au>, <JOHNSON@spam.DOMAIN.com.au>
Subject: Your Attention is Urgently Needed
Date: Thu, 15 Jun 2023 03:37:14 -0700
MIME-Version: 1.0
Content-Type: text/plain; charset="Windows-1251"
Content-Transfer-Encoding: quoted-printable
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2600.0000
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2600.0000
Message-ID: <44fe03c2-547d-454e-bdbc-128f69389bb5@MAIL2.payonline.space>
To: Undisclosed recipients:;
X-ClientProxiedBy: MAIL2.payonline.space (192.168.10.32) To
MAIL2.payonline.space (192.168.10.32)
X-SPAM-LEVEL: Spam detection results: 40
ADVANCE_FEE_3_NEW_FRM_MNY 0.001 Advance Fee fraud form and lots of money
AXB_XMAILER_MIMEOLE_OL_024C2 0.001 Yet another X header trait
BAYES_99 3.5 Bayes spam probability is 99 to 100%
BAYES_999 0.2 Bayes spam probability is 99.9 to 100%
DCC_CHECK 1.1 Detected as bulk mail by DCC (dcc-servers.net)
DCC_REPUT_99_100 5 DCC reputation between 99 % or higher (spam)
FILL_THIS_FORM 0.001 Fill in a form with personal information
FORGED_MUA_OUTLOOK 1.927 Forged mail pretending to be from MS Outlook
FREEMAIL_FORGED_REPLYTO 2.095 Freemail in Reply-To, but not From
FREEMAIL_REPLYTO_END_DIGIT 0.25 Reply-To freemail username ends in digit
FSL_BULK_SIG 0.001 Bulk signature with no Unsubscribe
FSL_CTYPE_WIN1251 0.001 Content-Type only seen in 419 spam
FSL_NEW_HELO_USER 0.001 Spam's using Helo and User
HK_SCAM 1.999 -
KAM_DMARC_STATUS 0.01 Test Rule for DKIM or SPF Failure with Strict Alignment
KAM_GB_INVALID_FROM 3 From Address is invalid
KHOP_HELO_FCRDNS 5 Relay HELO differs from its IP's reverse DNS
LOTS_OF_MONEY 0.001 Huge... sums of money
MONEY_FORM 0.001 Lots of money if you fill out a form
MONEY_FRAUD_3 0.001 Lots of money and several fraud phrases
MONEY_FREEMAIL_REPTO 0.49 Lots of money from someone using free email?
NSL_RCVD_FROM_USER 0.001 Received from User
OLV_HIDDEN 1 -
PYZOR_CHECK 1.392 Listed in Pyzor (https://pyzor.readthedocs.io/en/latest/)
RCVD_IN_HOSTKARMA_BL 2 Sender listed in HOSTKARMA-BLACK
RCVD_IN_SBL 0.141 Received via a relay in Spamhaus SBL
RELAYCOUNTRY_BAD 2 Email Originating from Untrusted Countries
SPAMMY_TLD_IN_RCVD 6 Spammy TLD used in Received line
SPF_HELO_NONE 0.001 SPF: HELO does not publish an SPF Record
T_SCC_BODY_TEXT_LINE -0.01 -
UNDISC_MONEY 2.899 Undisclosed recipients + money/fraud signs
Return-Path: <>
X-MS-Exchange-Organization-Network-Message-Id: 92a815ae-8c8d-4d18-1da7-08db6eab5a1b
Received-SPF: Fail (SERVER.internal.local: domain of invalid address does not
designate 192.168.000.000 as permitted sender) receiver=SERVER.internal.local;
client-ip=192.168.000.000; helo=spam.DOMAIN.com.au;
X-MS-Exchange-Organization-AVStamp-Enterprise: 1.0
X-MS-Exchange-Organization-AuthSource: SERVER.internal.local
X-MS-Exchange-Organization-AuthAs: Anonymous
X-MS-Exchange-Transport-EndToEndLatency: 00:00:00.2031926
X-MS-Exchange-Processed-By-BccFoldering: 15.01.2507.021SIMPLIFIED HEADER
Code:
Hop Delay From By With Time (UTC) Blacklist
1 * User 45.88.66.146 MAIL2.payonline.space 192.168.10.32 Microsoft SMTP Server (TLS) 6/15/2023 10:37:15 AM Is on a blacklist
2 1 days mail2.payonline.ru 91.205.9.213 spam.DOMAIN.com.au cipher ECDHE-RSA-AES256-SHA (256/256 bits)) (No client certificate requested) 6/16/2023 8:50:39 PM Is on a blacklist
3 4 seconds spam.DOMAIN.com.au 127.0.0.1 spam.DOMAIN.com.au ESMTP 6/16/2023 8:50:43 PM Not blacklisted
4 0 seconds spam.DOMAIN.com.au 192.168.000.000 SERVER.internal.local 192.168.000.000 Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384) 6/16/2023 8:50:43 PM Not blacklisted
5 0 seconds SERVER.internal.local 192.168.000.000 SERVER.internal.local 192.168.000.000 Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384) 6/16/2023 8:50:43 PM Not blacklisted
6 0 seconds SERVER.internal.local 192.168.000.000 SERVER.internal.local 192.168.000.000 Microsoft SMTP Server (version=TLS1_2, cipher=TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384) 6/16/2023 8:50:43 PM Not blacklistedSYSLOG
Code:
Jun 17 06:50:29 spam postfix/postscreen[2103961]: CONNECT from [91.205.9.213]:11455 to [192.168.18.17]:25
Jun 17 06:50:30 spam postfix/postscreen[2103961]: PASS OLD [91.205.9.213]:11455
Jun 17 06:50:31 spam postfix/smtpd[2104024]: connect from mail.payonline.ru[91.205.9.213]
Jun 17 06:50:33 spam postfix/smtpd[2104024]: Anonymous TLS connection established from mail.payonline.ru[91.205.9.213]: TLSv1 with cipher ECDHE-RSA-AES256-SHA (256/256 bits)
Jun 17 06:50:42 spam postfix/smtpd[2104024]: 29FCA180B24: client=mail.payonline.ru[91.205.9.213]
Jun 17 06:50:42 spam postfix/cleanup[2103973]: 29FCA180B24: info: header From: GLEN JOHNSON from mail.payonline.ru[91.205.9.213]; from=<> to=<helen@RECIPIENT.com.au> proto=ESMTP helo=<mail2.payonline.ru>
Jun 17 06:50:42 spam postfix/cleanup[2103973]: 29FCA180B24: info: header Subject: Your Attention is Urgently Needed from mail.payonline.ru[91.205.9.213]; from=<> to=<helen@RECIPIENT.com.au> proto=ESMTP helo=<mail2.payonline.ru>
Jun 17 06:50:42 spam postfix/cleanup[2103973]: 29FCA180B24: message-id=<44fe03c2-547d-454e-bdbc-128f69389bb5@MAIL2.payonline.space>
Jun 17 06:50:42 spam postfix/cleanup[2103973]: 29FCA180B24: info: header To: Undisclosed recipients:; from mail.payonline.ru[91.205.9.213]; from=<> to=<helen@RECIPIENT.com.au> proto=ESMTP helo=<mail2.payonline.ru>
Jun 17 06:50:42 spam postfix/qmgr[1326]: 29FCA180B24: from=<>, size=2112, nrcpt=1 (queue active)
Jun 17 06:50:42 spam pmg-smtp-filter[2103814]: 2023/06/17-06:50:42 CONNECT TCP Peer: "[127.0.0.1]:47970" Local: "[127.0.0.1]:10024"
Jun 17 06:50:42 spam pmg-smtp-filter[2103814]: 1A0331648CCB227A1F4: new mail message-id=<44fe03c2-547d-454e-bdbc-128f69389bb5@MAIL2.payonline.space>
Jun 17 06:50:42 spam postfix/smtpd[2104024]: disconnect from mail.payonline.ru[91.205.9.213] ehlo=2 starttls=1 mail=1 rcpt=1 bdat=1 quit=1 commands=7
Jun 17 06:50:42 spam systemd[1]: Starting Daily apt upgrade and clean activities...
Jun 17 06:50:43 spam systemd[1]: apt-daily-upgrade.service: Succeeded.
Jun 17 06:50:43 spam systemd[1]: Finished Daily apt upgrade and clean activities.
Jun 17 06:50:43 spam pmg-smtp-filter[2103814]: 1A0331648CCB227A1F4: SA score=40/5 time=0.601 bayes=1.00 autolearn=spam autolearn_force=no hits=ADVANCE_FEE_3_NEW_FRM_MNY(0.001),AXB_XMAILER_MIMEOLE_OL_024C2(0.001),BAYES_99(3.5),BAYES_999(0.2),DCC_CHECK(1.1),DCC_REPUT_99_100(5),FILL_THIS_FORM(0.001),FORGED_MUA_OUTLOOK(1.927),FREEMAIL_FORGED_REPLYTO(2.095),FREEMAIL_REPLYTO_END_DIGIT(0.25),FSL_BULK_SIG(0.001),FSL_CTYPE_WIN1251(0.001),FSL_NEW_HELO_USER(0.001),HK_SCAM(1.999),KAM_DMARC_STATUS(0.01),KAM_GB_INVALID_FROM(3),KHOP_HELO_FCRDNS(5),LOTS_OF_MONEY(0.001),MONEY_FORM(0.001),MONEY_FRAUD_3(0.001),MONEY_FREEMAIL_REPTO(0.49),NSL_RCVD_FROM_USER(0.001),OLV_HIDDEN(1),PYZOR_CHECK(1.392),RCVD_IN_HOSTKARMA_BL(2),RCVD_IN_SBL(0.141),RELAYCOUNTRY_BAD(2),SPAMMY_TLD_IN_RCVD(6),SPF_HELO_NONE(0.001),T_SCC_BODY_TEXT_LINE(-0.01),UNDISC_MONEY(2.899)
Jun 17 06:50:43 spam pmg-smtp-filter[2103814]: 1A0331648CCB227A1F4: sender in user (helen@RECIPIENT.com.au) welcomelist
Jun 17 06:50:43 spam pmg-smtp-filter[2103814]: 1A0331648CCB227A1F4: sender in user (helen@RECIPIENT.com.au) welcomelist
Jun 17 06:50:43 spam pmg-smtp-filter[2103814]: 1A0331648CCB227A1F4: sender in user (helen@RECIPIENT.com.au) welcomelist
Jun 17 06:50:43 spam pmg-smtp-filter[2103814]: 1A0331648CCB227A1F4: sender in user (helen@RECIPIENT.com.au) welcomelist
Jun 17 06:50:43 spam pmg-smtp-filter[2103814]: 1A0331648CCB227A1F4: sender in user (helen@RECIPIENT.com.au) welcomelist
Jun 17 06:50:43 spam postfix/smtpd[2103986]: connect from localhost.localdomain[127.0.0.1]
Jun 17 06:50:43 spam postfix/smtpd[2103986]: 41B16180BCE: client=localhost.localdomain[127.0.0.1], orig_client=mail.payonline.ru[91.205.9.213]
Jun 17 06:50:43 spam postfix/cleanup[2103973]: 41B16180BCE: message-id=<44fe03c2-547d-454e-bdbc-128f69389bb5@MAIL2.payonline.space>
Jun 17 06:50:43 spam postfix/qmgr[1326]: 41B16180BCE: from=<>, size=4484, nrcpt=1 (queue active)
Jun 17 06:50:43 spam postfix/smtpd[2103986]: disconnect from localhost.localdomain[127.0.0.1] ehlo=1 xforward=1 mail=1 rcpt=1 data=1 commands=5
Jun 17 06:50:43 spam pmg-smtp-filter[2103814]: 1A0331648CCB227A1F4: accept mail to <helen@RECIPIENT.com.au> (41B16180BCE) (rule: default-accept)
Jun 17 06:50:43 spam pmg-smtp-filter[2103814]: 1A0331648CCB227A1F4: processing time: 0.814 seconds (0.601, 0.035, 0.116)
Jun 17 06:50:43 spam postfix/lmtp[2103974]: 29FCA180B24: to=<helen@RECIPIENT.com.au>, relay=127.0.0.1[127.0.0.1]:10024, delay=3.6, delays=2.8/0/0.04/0.82, dsn=2.5.0, status=sent (250 2.5.0 OK (1A0331648CCB227A1F4))
Jun 17 06:50:43 spam postfix/qmgr[1326]: 29FCA180B24: removed
Jun 17 06:50:43 spam postfix/smtp[2103987]: Trusted TLS connection established to 192.168.000.000[192.168.000.000]:25: TLSv1.2 with cipher ECDHE-RSA-AES256-SHA384 (256/256 bits)
Jun 17 06:50:43 spam postfix/smtp[2103987]: 41B16180BCE: to=<helen@RECIPIENT.com.au>, relay=192.168.000.000[192.168.000.000]:25, delay=0.2, delays=0.05/0/0.02/0.13, dsn=2.6.0, status=sent (250 2.6.0 <44fe03c2-547d-454e-bdbc-128f69389bb5@MAIL2.payonline.space> [InternalId=268607254691912, Hostname=SERVER.internal.local] 6041 bytes in 0.110, 53.429 KB/sec Queued mail for delivery)
Jun 17 06:50:43 spam postfix/qmgr[1326]: 41B16180BCE: removedThe above shows that it has gone through the PMG spam.DOMAIN.com.au .. It shows in the SYSLOGS but does not show in the Tracking Centre.
It is clearly SPAM, but somehow it is allowed through?
The recipient does not have any whitelist. I have not stipulated any IP/DNS whitelisting for this origin in the custom.cf file or via GUI.
PMG is 7.3-3 (just updated to 7.3-4 just before I made this post).
Anyone recommend what actions I should consider?
Last edited: