Hi all, I'm trying to achieve the following:
Can't reach the internet but I can ping the gateway in the container:
Here is my /etc/network/interfaces:
- I have 2 public IPv4 addresses
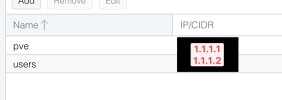
- 1.1.1.1 for the PVE host on enp0s31f6
- 1.1.1.2 for LXC & VMs on enp0s31f6:0
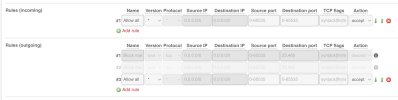
- I have a vmbr0 which must translate packets originating from 10.0.0.0/24 to 1.1.1.2 on enp0s31f6. This is so that containers and VMs are reachable to and from the internet via 1.1.1.2.
Can't reach the internet but I can ping the gateway in the container:
Code:
root@CT100:~# curl ifconfig.me
curl: (28) Failed to connect to ifconfig.me port 80 after 135718 ms: Couldn't connect to server
root@CT100:~# ping 10.0.0.1
PING 10.0.0.1 (10.0.0.1) 56(84) bytes of data.
64 bytes from 10.0.0.1: icmp_seq=1 ttl=64 time=0.040 ms
64 bytes from 10.0.0.1: icmp_seq=2 ttl=64 time=0.040 ms
64 bytes from 10.0.0.1: icmp_seq=3 ttl=64 time=0.040 ms
^C
--- 10.0.0.1 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2027ms
rtt min/avg/max/mdev = 0.040/0.040/0.040/0.000 msHere is my /etc/network/interfaces:
Code:
auto lo
iface lo inet loopback
auto enp0s31f6
allow-hotplug enp0s31f6
iface enp0s31f6 inet static
address 1.1.1.1/26
gateway 1.1.1.3
auto enp0s31f6:0
allow-hotplug enp0s31f6:0
iface enp0s31f6:0 inet static
address 1.1.1.2/26
auto vmbr0
iface vmbr0 inet static
address 10.0.0.1/24
bridge-ports none
bridge-stp off
bridge-fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s 10.0.0.0/24 -o enp0s31f6 -j SNAT --to-source 1.1.1.2
post-down iptables -t nat -D POSTROUTING -s 10.0.0.0/24 -o enp0s31f6 -j SNAT --to-source 1.1.1.2
source /etc/network/interfaces.d/*
Last edited: