Maybe it would be smart to at least allow access to only port 8006 on the "datacenter" firewall!!!!!!!
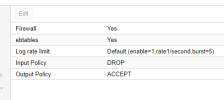
It's already open by default, so you can enable the firewall even with with "input policy" set to "DROP" or "REJECT". You only need manually to open that port in case you create a rule that explicitely blocks it, as custom rules got higher priority than the input/output policies or hidden default rules. See the hidden anti-lockout rules: https://pve.proxmox.com/wiki/Firewall#pve_firewall_default_rulesWhy don't they at least default port 8006 open when you turn the firewall on the data center.
Not true, i turned mine on the "datacenter", not the master and it locked me out until i added those rules. I had to get with the NOC to shut the firewall back off.It's already open by default, so you can enable the firewall even with with "input policy" set to "DROP" or "REJECT". You only need manually to open that port in case you create a rule that explicitely blocks it, as custom rules got hogher priority than the input/output policies or hidden default rules. See the hidden anti-lockout rules: https://pve.proxmox.com/wiki/Firewall#pve_firewall_default_rules
We use essential cookies to make this site work, and optional cookies to enhance your experience.

