Full disclosure: I'm running an old version of Proxmox 3.4 which I have been planning to update to 4.x but haven't got around to yet. The server is colocated at a datacenter in the Netherlands and I have access via an iDRAC (Dell IPMI system). I have very limited linux knowledge, so please forgive my ignorance.
The server runs a number of VMs, all of which are KVM, mainly for the purposes of hosting websites. It was running perfectly fine until earlier today when I received a system email:
I'm used to getting such emails when I update the system myself, but I hadn't logged in recently. The server was unresponsive to ping, so I had the datacenter reboot the system. No change.
I used the iDRAC to reboot the system myself so I could watch the startup sequence and was eventually presented with the message below.
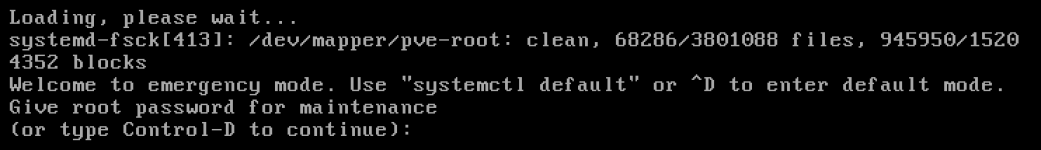
I entered the root password and tried to follow what the prompt said. I ran systemctrl default and got the following message.
When I ran journalctl I got the message "command not found".
Has anyone got any ideas?
At this stage, since I have no idea what's wrong, all I want to do is see if I can get the vm images off and onto another server. Do you think I could do this using a live cd and if so, how would I go about it?
I would appreciate any help people could provide.
The server runs a number of VMs, all of which are KVM, mainly for the purposes of hosting websites. It was running perfectly fine until earlier today when I received a system email:
Code:
wget (1.13.4-3+deb7u3) wheezy-security; urgency=high
This version fixes a security vulnerability (CVE-2016-4971) present
in all old versions of wget. The vulnerability was discovered by
Dawid Golunski which were reported to us by Beyond Security's
SecuriTeam.
On a server redirect from HTTP to a FTP resource, wget would trust the
HTTP server and uses the name in the redirected URL as the destination
filename.
This behaviour was changed and now it works similarly as a redirect
from HTTP to another HTTP resource so the original name is used as
the destination file. To keep the previous behaviour the user must
provide --trust-server-names.
-- Thorsten Alteholz <debian@alteholz.de> Mon, 27 Jun 2016 18:00:14 +0200I'm used to getting such emails when I update the system myself, but I hadn't logged in recently. The server was unresponsive to ping, so I had the datacenter reboot the system. No change.
I used the iDRAC to reboot the system myself so I could watch the startup sequence and was eventually presented with the message below.

I entered the root password and tried to follow what the prompt said. I ran systemctrl default and got the following message.
Code:
Failed to get D-Bus connection: No connection to service managerWhen I ran journalctl I got the message "command not found".
Has anyone got any ideas?
At this stage, since I have no idea what's wrong, all I want to do is see if I can get the vm images off and onto another server. Do you think I could do this using a live cd and if so, how would I go about it?
I would appreciate any help people could provide.

