I have 1 Linux bridge, vmbr0, which Security Onion is using as the Management interface via the net0 network card. I have 2 additional OVS bridges, vmbr1 and vmbr2.
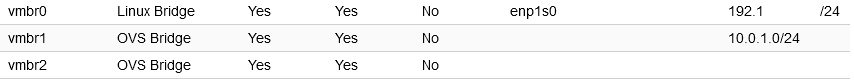
I have connected the Security Onion sniffing interface, net1, to vmbr1. The Security Onion VM ID is 101.
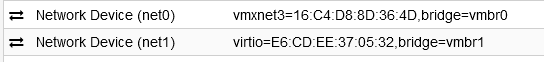
I have a Kali and Ubuntu VMs each with a single network card connected to vmbr2.
Kali:
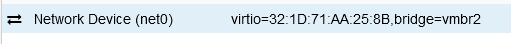
Ubuntu:

I then run the command below to enable the mirroring:
ovs-vsctl -- --id=@p get port tap101i1 -- --id=@m create mirror name=span2 select-all=true output-port=@p -- set bridge vmbr2 mirrors=@m
The problem am facing is that with the setup above, I cannot receive any traffic on the SecOnion VM using 'sudo tcpdump -i ens19 -v '.
However, when I put the Kali and Ubuntu VMs on the same bridge, vmbr1, as the SecOnion sniffing interface and enable mirroring using:
ovs-vsctl -- --id=@p get port tap101i1 -- --id=@m create mirror name=span1 select-all=true output-port=@p -- set bridge vmbr1 mirrors=@m
I can capture the traffic between the 2 VMs on the SecOnion sniffing interface using 'sudo tcpdump -i ens19 -v '.
I followed the guidelines provided in https://vext.info/2018/09/03/cheat-sheet-port-mirroring-ids-data-into-a-proxmox-vm.html and several other sources.
I would like/prefer to use 2 separate OVS bridges in my setup. 1, vmbr1, for SecOnion sniffing only and 2, vmbr2, for the VMs whose traffic I'd like to monitor.
I have tried using different network cards (virtIO, e1000, vmxnet3), checked and confirmed no firewalls or filters are up but am still unable to capture traffic using the setup that I prefer. I would appreciate your help on resolving this one.
My /etc/network/interfaces looks like this:
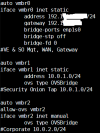
Please help.

I have connected the Security Onion sniffing interface, net1, to vmbr1. The Security Onion VM ID is 101.

I have a Kali and Ubuntu VMs each with a single network card connected to vmbr2.
Kali:
Ubuntu:
I then run the command below to enable the mirroring:
ovs-vsctl -- --id=@p get port tap101i1 -- --id=@m create mirror name=span2 select-all=true output-port=@p -- set bridge vmbr2 mirrors=@m
The problem am facing is that with the setup above, I cannot receive any traffic on the SecOnion VM using 'sudo tcpdump -i ens19 -v '.
However, when I put the Kali and Ubuntu VMs on the same bridge, vmbr1, as the SecOnion sniffing interface and enable mirroring using:
ovs-vsctl -- --id=@p get port tap101i1 -- --id=@m create mirror name=span1 select-all=true output-port=@p -- set bridge vmbr1 mirrors=@m
I can capture the traffic between the 2 VMs on the SecOnion sniffing interface using 'sudo tcpdump -i ens19 -v '.
I followed the guidelines provided in https://vext.info/2018/09/03/cheat-sheet-port-mirroring-ids-data-into-a-proxmox-vm.html and several other sources.
I would like/prefer to use 2 separate OVS bridges in my setup. 1, vmbr1, for SecOnion sniffing only and 2, vmbr2, for the VMs whose traffic I'd like to monitor.
I have tried using different network cards (virtIO, e1000, vmxnet3), checked and confirmed no firewalls or filters are up but am still unable to capture traffic using the setup that I prefer. I would appreciate your help on resolving this one.
My /etc/network/interfaces looks like this:

Please help.
Attachments
Last edited:

