Hello,
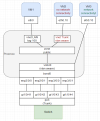
Looking for guidance on how to enable trunking/tagging on an SDN VNet. Use case is pictured below.
Host is bonded to a switch over 4x interfaces, vmbr0 has bond0 as a member and is vlan aware.
There is an SDN zone named "Public" that has vmbr0 as the bridge.
There are multiple vnets with tags that reference the Public zone and all of them are working fine (eg. VM1)
What I'm trying to do is create a VNet that can "pass the trunk" to a VM (eg. VM2). I thought all I would have to do is enable "vlan aware" for the Trunk vnet but it forces me to also add a tag...which confuses me. Makes me think its a q-in-q type setup which is not going to work. Regardless, when I attach VM2 to this vnet I get no network connectivity.
However, if I bypass SDN completely and configure vmbr0 as the bridge on the VM port I get network connectivity (eg. VM3) which tells me the issue is on the SDN side somewhere.
I spin up a lot of networking VMs and being able to use sub-interfaces on the fly is huge. While the vmbr0 mapping works I would prefer to keep all my network mappings within the SDN space if possible. Thanks in advance!
Looking for guidance on how to enable trunking/tagging on an SDN VNet. Use case is pictured below.
Host is bonded to a switch over 4x interfaces, vmbr0 has bond0 as a member and is vlan aware.
There is an SDN zone named "Public" that has vmbr0 as the bridge.
There are multiple vnets with tags that reference the Public zone and all of them are working fine (eg. VM1)
What I'm trying to do is create a VNet that can "pass the trunk" to a VM (eg. VM2). I thought all I would have to do is enable "vlan aware" for the Trunk vnet but it forces me to also add a tag...which confuses me. Makes me think its a q-in-q type setup which is not going to work. Regardless, when I attach VM2 to this vnet I get no network connectivity.
However, if I bypass SDN completely and configure vmbr0 as the bridge on the VM port I get network connectivity (eg. VM3) which tells me the issue is on the SDN side somewhere.
I spin up a lot of networking VMs and being able to use sub-interfaces on the fly is huge. While the vmbr0 mapping works I would prefer to keep all my network mappings within the SDN space if possible. Thanks in advance!


