hello all
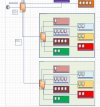
i try to do following. as in the picture seen, i need to zones (one is the windows network with 172.15.101-110 and the other the Openshift Network with 172.1.199.100-110)
the windows network is only on server which need to connect to the internet and 3 to other servers in other zones. the same for the openshift network
i created 2 Controllers (lets call them A and B), 2 Zones (lets call them 1 and 2) and the dependent Vnets (lets call them ! and ?).
the chain is
A <> 1 <> !
and
B <> 2 <> ?
here are some questions
1. Multiple VNets vs single Vnet and multiple Subnets ?
means: Vnet win100, win101, win102, and so on and vnet OpnSft100, OpnSft101, OpnSft102, and so on
or Vnet WinvNet with subnets 100, 101, 102, and so on and for the Openshift the same
as iunderstood: the subnets in the vNets can communicate out of box to each other vs with multiple VNets i need a router (opnsense) between - correct ?
what is the best way to archive te challange ?
2. to connect to "outside" (and it would mean already between 2 different zones or to any other service (like a centralized DNS) i need an exit host - is that correct ?
but dont i leave than the "secure" environment ?
i want in front the the windows network an opnsense for firewalling (no traffic is allowed in and out / only DNS and 3 servers will connect to another Server in the public area)
3. in the econtroler config is ask for "peers" and in the evpn config ask for exit nodes - isnt that the same ?
thx for answers
i try to do following. as in the picture seen, i need to zones (one is the windows network with 172.15.101-110 and the other the Openshift Network with 172.1.199.100-110)
the windows network is only on server which need to connect to the internet and 3 to other servers in other zones. the same for the openshift network
i created 2 Controllers (lets call them A and B), 2 Zones (lets call them 1 and 2) and the dependent Vnets (lets call them ! and ?).
the chain is
A <> 1 <> !
and
B <> 2 <> ?
here are some questions
1. Multiple VNets vs single Vnet and multiple Subnets ?
means: Vnet win100, win101, win102, and so on and vnet OpnSft100, OpnSft101, OpnSft102, and so on
or Vnet WinvNet with subnets 100, 101, 102, and so on and for the Openshift the same
as iunderstood: the subnets in the vNets can communicate out of box to each other vs with multiple VNets i need a router (opnsense) between - correct ?
what is the best way to archive te challange ?
2. to connect to "outside" (and it would mean already between 2 different zones or to any other service (like a centralized DNS) i need an exit host - is that correct ?
but dont i leave than the "secure" environment ?
i want in front the the windows network an opnsense for firewalling (no traffic is allowed in and out / only DNS and 3 servers will connect to another Server in the public area)
3. in the econtroler config is ask for "peers" and in the evpn config ask for exit nodes - isnt that the same ?
thx for answers
Attachments
Last edited: