Hey all
Previously my networking was as follows
vmbr0 attached to eth1 - vmbr0 used for management IP. Management vlan is untagged.
vmbr110 attached to eth1.110 - no ip on host
vmbr120 attached to eth1.120 - no ip on host
vmbr130 attached to eth1.130 - no ip on host
etc to use for guest networking as appropriate.
These vmbr devices were all configured in /etc/network/interfaces.
I've installed and set up the SDN packages to try to simplify my network management moving forward...
Has anyone seen this kind of behaviour before and/or know how to fix it?
Previously my networking was as follows
vmbr0 attached to eth1 - vmbr0 used for management IP. Management vlan is untagged.
vmbr110 attached to eth1.110 - no ip on host
vmbr120 attached to eth1.120 - no ip on host
vmbr130 attached to eth1.130 - no ip on host
etc to use for guest networking as appropriate.
These vmbr devices were all configured in /etc/network/interfaces.
I've installed and set up the SDN packages to try to simplify my network management moving forward...
- I've removed all the extra vmbr11x and eth1.xx devices from /etc/network/interfaces
- I've made vmbr0 vlan aware
- I've added a single (vlan) zone to proxmox, using vmbr0 as the bridge
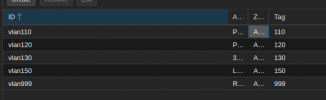
- I've added new vnets using sdn interface - vlan110 with a tag of 110, vlan120 with a tag of 120 etc
- moved all my guest networks to the new interfaces
Code:
# brctl show
bridge name bridge id STP enabled interfaces
vlan110 8000.00221965528e no tap143i0
veth138i0
vmbr0.110
vlan120 8000.00221965528e no veth274i0
veth277i0
vmbr0.120
vlan130 8000.00221965528e no vmbr0.130
vlan150 8000.00221965528e no tap501i0
tap9901i1
vmbr0.150
vlan999 8000.00221965528e no tap9901i0
vmbr0.999
vmbr0 8000.00221965528e no eth1
tap901i0Has anyone seen this kind of behaviour before and/or know how to fix it?
Last edited: