Looking to understand how can I get QinQ working with an OVS bridge.
My topology looks like this:
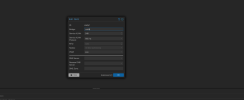
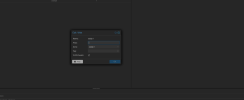
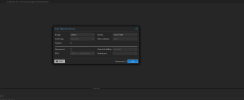
VM (will send tagged and untagged packets) --> TAP itf (configured with outer tag on proxomox UI) --> OVS bridge --> physical NIC --> C9300 Switch (which is configured to act in dot1q-tunnel mode)
Currently if I send untagged packets from VM they work fine and the outer tag is added correctly by the tap itf and forwarded out via the bridge to the physical itf. However when I send tagged packets I see them on the capture on the tap itf but not on the bridge. Making me think that the tap is dropping them as the inner tag does not match the outer tag. Is that a correct understanding?
If yes how can I setup OVS bridge to double tag packets?
Appreciate any help in this regard! Thanks in advance!
My topology looks like this:
VM (will send tagged and untagged packets) --> TAP itf (configured with outer tag on proxomox UI) --> OVS bridge --> physical NIC --> C9300 Switch (which is configured to act in dot1q-tunnel mode)
Currently if I send untagged packets from VM they work fine and the outer tag is added correctly by the tap itf and forwarded out via the bridge to the physical itf. However when I send tagged packets I see them on the capture on the tap itf but not on the bridge. Making me think that the tap is dropping them as the inner tag does not match the outer tag. Is that a correct understanding?
If yes how can I setup OVS bridge to double tag packets?
Appreciate any help in this regard! Thanks in advance!
Last edited: