I am quite new to vLANs so please forgive me of my terminology is off.
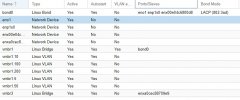
Today I have pfSense running as a VM on Proxmox (on a computer with 5 NICs), which is working great and up until now I have only been using subnets as I have not had any vLAN aware equipment. However, I have now bought some Unifi switches and APs that supports vLAN for better segmentation of my network. There are many articles and guides on how to set up vLAN with pfSense, but I am not sure what changes I need to do on the Proxmox side. Below is the way my network interfaces are configured in Proxmox today as well as a diagram of how I'm picturing the physical setup with the new equipment.
The physical interfaces in use today will be the same, however, instead of each of the lan ports (SEC/IOT) being assigned to a separate subnet in pfSense and each connected to a unmanaged switch, they should now each trunk all vLANs defined in pfSense and connect to a managed vLAN-aware switch. Proxmox is also running a couple of other VM machines assigned the SEC interface. However, when changing over to vLAN I guess these needs to be assigned to the correct vLAN.
I would really appreciate some input / comments on what changes I need to do in Proxmox (if any) to get this to work.
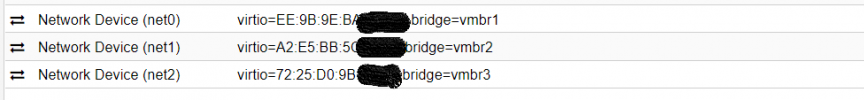
Proxmox network interfaces.
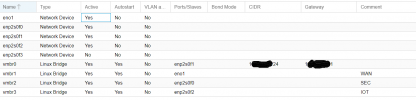
pfSense VM network interfaces
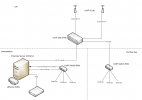
Today I have pfSense running as a VM on Proxmox (on a computer with 5 NICs), which is working great and up until now I have only been using subnets as I have not had any vLAN aware equipment. However, I have now bought some Unifi switches and APs that supports vLAN for better segmentation of my network. There are many articles and guides on how to set up vLAN with pfSense, but I am not sure what changes I need to do on the Proxmox side. Below is the way my network interfaces are configured in Proxmox today as well as a diagram of how I'm picturing the physical setup with the new equipment.
The physical interfaces in use today will be the same, however, instead of each of the lan ports (SEC/IOT) being assigned to a separate subnet in pfSense and each connected to a unmanaged switch, they should now each trunk all vLANs defined in pfSense and connect to a managed vLAN-aware switch. Proxmox is also running a couple of other VM machines assigned the SEC interface. However, when changing over to vLAN I guess these needs to be assigned to the correct vLAN.
I would really appreciate some input / comments on what changes I need to do in Proxmox (if any) to get this to work.
Proxmox network interfaces.

pfSense VM network interfaces