Proxmox 8.3.2, recent install.
The host has a single NIC, routing enabled and the VMs are connected to two OVS bridges without physical interfaces.
One Bridge uses VLAN tags, and the other doesn't. It happens on both, so I think this is irrelevant.
Two clients: OPNsense (BSD) and Fedora, are both affected in the same way.
The networking service isn't restarted often, but as I'm building VMs and configuring the host this is still an occurrence. However, the same happens when the host is rebooted. This would mean that without manual intervention all VMs would remain disconnected.
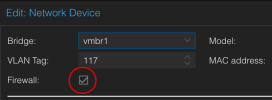
I've disabled the Datacenter firewall to see if that makes any difference, but it doesn't. I've seen some references to the VM network device config firewall setting breaking connectivity. But for me it doesn't matter which way the toggle is set. It'll break and switching this toggle brings connectivity back. I'm stumped...
The host has a single NIC, routing enabled and the VMs are connected to two OVS bridges without physical interfaces.
One Bridge uses VLAN tags, and the other doesn't. It happens on both, so I think this is irrelevant.
Two clients: OPNsense (BSD) and Fedora, are both affected in the same way.
The networking service isn't restarted often, but as I'm building VMs and configuring the host this is still an occurrence. However, the same happens when the host is rebooted. This would mean that without manual intervention all VMs would remain disconnected.
I've disabled the Datacenter firewall to see if that makes any difference, but it doesn't. I've seen some references to the VM network device config firewall setting breaking connectivity. But for me it doesn't matter which way the toggle is set. It'll break and switching this toggle brings connectivity back. I'm stumped...