Working solution: RTL8157 (Wisdpi WP-UT5) on Proxmox VE 9 with r8152 DKMS
I’ve got the Wisdpi WP-UT5 (RTL8157) running cleanly on PVE 9 using the awesometic r8152 DKMS driver, with Secure Boot MOK enrollment and automatic cdc_* blacklisting. I wrapped the steps into a safe one-shot script that handles:
- temporary failover of
vmbr0 to onboard NIC during the switch
- DKMS install for the running kernel
- MOK enrollment if Secure Boot is on
- driver rebind (prompt to unplug/replug once)
- restore
vmbr0 to the USB NIC and print a concise report
Script (auto-fetches latest
.deb if not present, or you can just download awesometic's
realtek-r8152-dkms_2.20.1-1_amd64.deb to
/root/ and run if there are issues):
https://github.com/aioue/r8152_proxmox_setup/blob/main/r8152_proxmox_setup.sh
Hardware
- USB NIC: Wisdpi WP-UT5 (Realtek RTL8157)
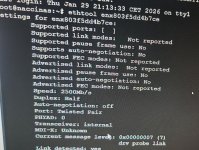
- Link: 5 Gbps, Full Duplex (validated with ethtool)
Software/Host
Code:
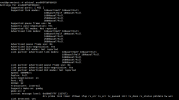
# pveversion
pve-manager/9.0.10 (running kernel: 6.14.11-2-pve)
# uname -a
Linux pve 6.14.11-2-pve #1 SMP PREEMPT_DYNAMIC PMX 6.14.11-2 (2025-09-12T09:46Z) x86_64 GNU/Linux
- Headers installed:
proxmox-headers-6.14.11-2-pve
- Secure Boot: Enabled; DKMS MOK enrolled (script prompts and handles import)
- Driver:
Code:
# ethtool -i enxXXXXXXXXXXXX
driver: r8152
version: v2.20.1 (2025/05/13)
bus-info: usb-0000:05:00.4-1
- Bind check:
Code:
# lsusb -t (excerpt)
|__ Port 001: Dev N, If 0, Class=Vendor Specific Class, Driver=r8152, 5000M
-
/etc/network/interfaces updated so
vmbr0 bridges the USB NIC;
hwaddress set to avoid MAC flips.
Notes
- The script blacklists
cdc_ncm,
cdc_ether,
r8153_ecm and updates initramfs so
r8152 binds first.
- If Secure Boot is enabled, you’ll be prompted to enroll the DKMS key (MOK) and reboot once; rerun the script after the reboot to complete.
- Requires onboard NIC (default
enp3s0) to be cabled during the switch so management stays up.
If you move to kernels ≥ 6.16 and hit API changes, consider the
wget fork of r8152 DKMS. With MOK already enrolled, it should load cleanly as well.