Hello!
After setting up a Cloudflare API-baesd custom certificate for the domain pve.myhost.com, everything works, and my certificate list looks like this.
The one at the bottom is the custom ceriticate I created.
What are the first two? Does it create problems to leave them there? The second one in particular has a ton of Alternate Names listed, including an IP address. Putting aside for a moment the fact that I didn't know you could list an IP address on a certificate like this--I don't think Cloudflare's API lets you do that--it's also listing an IP that isn't in use with the PVE server anymore, as well as pve without the .myhost.com. It also lists pve.myhost.local, which isn't even a valid TLD in my LAN anymore.
Thanks for any advice.
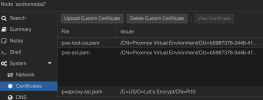
After setting up a Cloudflare API-baesd custom certificate for the domain pve.myhost.com, everything works, and my certificate list looks like this.
The one at the bottom is the custom ceriticate I created.
What are the first two? Does it create problems to leave them there? The second one in particular has a ton of Alternate Names listed, including an IP address. Putting aside for a moment the fact that I didn't know you could list an IP address on a certificate like this--I don't think Cloudflare's API lets you do that--it's also listing an IP that isn't in use with the PVE server anymore, as well as pve without the .myhost.com. It also lists pve.myhost.local, which isn't even a valid TLD in my LAN anymore.
- I think the second one is just Proxmox's default self-signed certificate? No action needed?
- But, I have no idea what's going on with the second one and if I need to do anything to clean it up.
- Also, is it possible to actually have a Let's Encrypt-issued certificate for pve without myhost.com? Can I list pve or just the IP as an alternate name when I'm using the Cloudflare API to get the Let's Encrypt cert? Will Cloudflare's API even let me do that?
Thanks for any advice.


