chiming in, because I stumbled across a similar problem. (hi
@Ne00n ;-))
it seems like DENY_FROM and ALLOW_FROM settings in /etc/default/pveproxy are sometimes ignored at all, esp. with newer releases of proxmox.
I checked on three different systems running different builds. it only works on an older one as expected and described on the man page.
always used the entries like in the usual example:
Code:
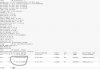
# cat /etc/default/pveproxy
ALLOW_FROM="127.0.0.1"
DENY_FROM="all"
POLICY="allow"
pveversion and netstat from the one were this is still working and restricting access as expected:
Code:
# pveversion -v
proxmox-ve: 4.4-80 (running kernel: 4.4.40-1-pve)
pve-manager: 4.4-12 (running version: 4.4-12/e71b7a74)
pve-kernel-4.4.35-1-pve: 4.4.35-77
pve-kernel-4.4.35-2-pve: 4.4.35-79
pve-kernel-4.4.21-1-pve: 4.4.21-71
pve-kernel-4.4.16-1-pve: 4.4.16-64
pve-kernel-4.4.19-1-pve: 4.4.19-66
pve-kernel-4.4.40-1-pve: 4.4.40-80
lvm2: 2.02.116-pve3
corosync-pve: 2.4.2-1
libqb0: 1.0-1
pve-cluster: 4.0-48
qemu-server: 4.0-109
pve-firmware: 1.1-10
libpve-common-perl: 4.0-92
libpve-access-control: 4.0-23
libpve-storage-perl: 4.0-73
pve-libspice-server1: 0.12.8-1
vncterm: 1.3-1
pve-docs: 4.4-3
pve-qemu-kvm: 2.7.1-3
pve-container: 1.0-94
pve-firewall: 2.0-33
pve-ha-manager: 1.0-40
ksm-control-daemon: 1.2-1
glusterfs-client: 3.9.1-1
Code:
# netstat -tulpen
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State User Inode PID/Program name
tcp 0 0 127.0.0.1:85 0.0.0.0:* LISTEN 0 18483 1370/pvedaemon
tcp 0 0 0.0.0.0:3128 0.0.0.0:* LISTEN 33 33830822 26168/spiceproxy
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 0 17686 1336/master
tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN 0 1703 1235/nginx -g daemo
tcp 0 0 0.0.0.0:55266 0.0.0.0:* LISTEN 106 9952 973/rpc.statd
tcp 0 0 0.0.0.0:8006 0.0.0.0:* LISTEN 33 34625375 3278/pveproxy
tcp 0 0 0.0.0.0:36934 0.0.0.0:* LISTEN 0 20686 -
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 0 9879 956/rpcbind
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 0 1702 1235/nginx -g daemo
tcp6 0 0 :::60341 :::* LISTEN 106 9956 973/rpc.statd
tcp6 0 0 :::25 :::* LISTEN 0 17687 1336/master
tcp6 0 0 :::46491 :::* LISTEN 0 20688 -
tcp6 0 0 :::111 :::* LISTEN 0 9883 956/rpcbind
on a slightly newer one, it's ignoring the try to force to localhost only:
Code:
# pveversion -v
proxmox-ve: 4.4-86 (running kernel: 4.4.49-1-pve)
pve-manager: 4.4-13 (running version: 4.4-13/7ea56165)
pve-kernel-4.4.49-1-pve: 4.4.49-86
pve-kernel-4.4.40-1-pve: 4.4.40-82
lvm2: 2.02.116-pve3
corosync-pve: 2.4.2-2~pve4+1
libqb0: 1.0.1-1
pve-cluster: 4.0-49
qemu-server: 4.0-110
pve-firmware: 1.1-11
libpve-common-perl: 4.0-94
libpve-access-control: 4.0-23
libpve-storage-perl: 4.0-76
pve-libspice-server1: 0.12.8-2
vncterm: 1.3-2
pve-docs: 4.4-4
pve-qemu-kvm: 2.7.1-4
pve-container: 1.0-97
pve-firewall: 2.0-33
pve-ha-manager: 1.0-40
ksm-control-daemon: 1.2-1
glusterfs-client: 3.9.1-1
lxc-pve: 2.0.7-4
lxcfs: 2.0.6-pve1
criu: 1.6.0-1
novnc-pve: 0.5-9
smartmontools: 6.5+svn4324-1~pve80
Code:
# netstat -tulpen
Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State User Inode PID/Program name
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 0 23643 1761/master
tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN 0 21627316 12535/nginx -g daem
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 0 20798 1327/rpcbind
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 0 21627315 12535/nginx -g daem
tcp 0 0 127.0.0.1:85 0.0.0.0:* LISTEN 0 105505112 3602/pvedaemon
tcp 0 0 0.0.0.0:37622 0.0.0.0:* LISTEN 103 17501 1351/rpc.statd
tcp6 0 0 :::3128 :::* LISTEN 33 105404936 18694/spiceproxy
tcp6 0 0 :::25 :::* LISTEN 0 23644 1761/master
tcp6 0 0 :::34595 :::* LISTEN 103 17505 1351/rpc.statd
tcp6 0 0 :::8006 :::* LISTEN 33 105531728 7327/pveproxy
tcp6 0 0 :::111 :::* LISTEN 0 20802 1327/rpcbind
I tried to block IPv6 via ip6tables to make sure it's not the way it goes around, but I still could access the webinterface publicly on port 8006 ...
blocking the port via iptables always works (only that's just not the intended way here).
also changing the policy to deny works, so /etc/default/pveproxy gots read and interpreted after al, but the ALLOW_FROM still gets ignored then, so no access from locahost even.
I also tried this on pve 5.1. and got the same result, it doesn't get restricted to localhost anymore with the suggested way...
PS: I coincidentically just setting up another node, and deployed the newest build. On this node it is working as expected, only difference I could spot so far if the lack of IPv6 which isn't configured yet...
Code:
# pveversion -v
proxmox-ve: 5.1-32 (running kernel: 4.13.13-2-pve)
pve-manager: 5.1-41 (running version: 5.1-41/0b958203)
pve-kernel-4.13.13-2-pve: 4.13.13-32
pve-kernel-4.13.13-1-pve: 4.13.13-31
libpve-http-server-perl: 2.0-8
lvm2: 2.02.168-pve6
corosync: 2.4.2-pve3
libqb0: 1.0.1-1
pve-cluster: 5.0-19
qemu-server: 5.0-18
pve-firmware: 2.0-3
libpve-common-perl: 5.0-25
libpve-guest-common-perl: 2.0-14
libpve-access-control: 5.0-7
libpve-storage-perl: 5.0-17
pve-libspice-server1: 0.12.8-3
vncterm: 1.5-3
pve-docs: 5.1-12
pve-qemu-kvm: 2.9.1-5
pve-container: 2.0-18
pve-firewall: 3.0-5
pve-ha-manager: 2.0-4
ksm-control-daemon: not correctly installed
glusterfs-client: 3.8.8-1
lxc-pve: 2.1.1-2
lxcfs: 2.0.8-1
criu: 2.11.1-1~bpo90
novnc-pve: 0.6-4
smartmontools: 6.5+svn4324-1
Code:
# netstat -tulpen
Aktive Internetverbindungen (Nur Server)
Proto Recv-Q Send-Q Local Address Foreign Address State Benutzer Inode PID/Program name
tcp 0 0 127.0.0.1:85 0.0.0.0:* LISTEN 0 20740 1551/pvedaemon
tcp 0 0 0.0.0.0:3128 0.0.0.0:* LISTEN 33 22827 1630/spiceproxy
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN 0 22559 1474/master
tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN 0 19401 1273/nginx: master
tcp 0 0 0.0.0.0:8006 0.0.0.0:* LISTEN 33 20818 1599/pveproxy
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 0 2582 784/rpcbind
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 0 19400 1273/nginx: master
tcp6 0 0 :::25 :::* LISTEN 0 22560 1474/master
tcp6 0 0 :::111 :::* LISTEN 0 2585 784/rpcbind
so maybe IPv6 really is the issue here, making the port publicly available again? will have a further look into this, once I configure IPv6...