Hey all,
This might be something dumb i missed while configuring VLANs on the host but here it goes...
I have 5 VLANs on my network (10=PCs, 20=Laptops, 30=Printers, 40=Servers & 50=Management). I have 3 swiches and 3 PVEs on VLAN 40 and all the VMs on the same VLAN 40 inside the hosts since they are servers as well (Domain controller, File Server, etc.). I had the ports on the switch to access but with VLAN 40 and I had not configured the VLAN Aware at the bridge since everything work. Forward to this past week and now I have to create VMs that are not servers with VLAN 10 within the PVEs for testing configurations instead of using physical hardware and I can't ping the VMs inside the host. The changes I did are as follows:
- On the switches I configured the ports that previously were "access VLAN 40" to trunks passing all VLANS.
- On the PVEs I configured VMBR0 to be VLAN Aware
- I tagged all servers withing the PVEs with 40 as that is the VLAN they should be
- I created VMBR0.40 on each of the PVEs and gave it their respective IPs for each host
- I removed the hosts IP configuration from VMBR0 as it is supposed to be attached to the newly created VMBR0.40
Now i can ping everything on the network minus the Server VMs (VLAN 40) and the Test VM (VLAN 10) within the PVEs. Was there something I missed? It worked before the trunking of the ports because I guess everything inside the hosts was VLAN 40 and the hosts as well. All VMs are attached to VMBR0 now and the PVEs are attached to VMBR0.40.... is this ok? Do I have to create more VLAN intefaces for communication between VLANs or VMs and the network?
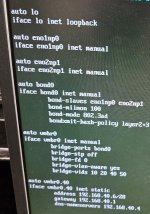
Attached is what I have for one of the PVEs but the rest of the have the same configuration, only diference is the IP for each PVE.
This might be something dumb i missed while configuring VLANs on the host but here it goes...
I have 5 VLANs on my network (10=PCs, 20=Laptops, 30=Printers, 40=Servers & 50=Management). I have 3 swiches and 3 PVEs on VLAN 40 and all the VMs on the same VLAN 40 inside the hosts since they are servers as well (Domain controller, File Server, etc.). I had the ports on the switch to access but with VLAN 40 and I had not configured the VLAN Aware at the bridge since everything work. Forward to this past week and now I have to create VMs that are not servers with VLAN 10 within the PVEs for testing configurations instead of using physical hardware and I can't ping the VMs inside the host. The changes I did are as follows:
- On the switches I configured the ports that previously were "access VLAN 40" to trunks passing all VLANS.
- On the PVEs I configured VMBR0 to be VLAN Aware
- I tagged all servers withing the PVEs with 40 as that is the VLAN they should be
- I created VMBR0.40 on each of the PVEs and gave it their respective IPs for each host
- I removed the hosts IP configuration from VMBR0 as it is supposed to be attached to the newly created VMBR0.40
Now i can ping everything on the network minus the Server VMs (VLAN 40) and the Test VM (VLAN 10) within the PVEs. Was there something I missed? It worked before the trunking of the ports because I guess everything inside the hosts was VLAN 40 and the hosts as well. All VMs are attached to VMBR0 now and the PVEs are attached to VMBR0.40.... is this ok? Do I have to create more VLAN intefaces for communication between VLANs or VMs and the network?
Attached is what I have for one of the PVEs but the rest of the have the same configuration, only diference is the IP for each PVE.