Hello,
I was trying to set some firewall rules to stop a VM from talking to other VMs but to allow it to reach the internet.
What I did:
1. Enabled the firewall at the datacenter level
2. Enabled the firewall on the VM NIC
3. Enable the firewall on the VM
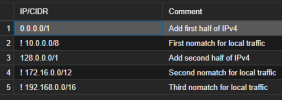
4. Create an IPSet for non local IPs called non_local, with these "IPs"
5. Create a Security Group with the following rules:
Rule 1:
Rule 2:
The issue is that this doesn't work for some reason and I don't understand why. From my point of view, it should allow all INCOMING traffic that's not coming from those private IPs and allow all OUTGOING traffic since none of that is going to the private IPs.
Also, just as a suggestion: can't we have a checkbox next to Src/DST saying "Don't match"? I'm asking because, for example, if I want to have two rules, one to match an IP and the other to match everything but that IP, I'd have to have two IPSets, one with the IP address and one with the IP non-match setting on.
Providing the cluster.fw file and vm_id.fw files down below for reference if needed
Also, just referencing this, maybe it gets more views, as I find it quite important...
https://forum.proxmox.com/threads/pve-8-pve-firewall-status-no-such-alias.130202/#post-573149
Thanks in advance.
I was trying to set some firewall rules to stop a VM from talking to other VMs but to allow it to reach the internet.
What I did:
1. Enabled the firewall at the datacenter level
2. Enabled the firewall on the VM NIC
3. Enable the firewall on the VM
4. Create an IPSet for non local IPs called non_local, with these "IPs"
Code:
!10.0.0.0/8
!172.16.0.0/12
!192.168.0.0/16Rule 1:
Code:
Direction: IN
Action: ACCEPT
Source: +dc/non-Local
Source:
Code:
Direction: OUT
Action: ACCEPT
Destination: +dc/non-localAlso, just as a suggestion: can't we have a checkbox next to Src/DST saying "Don't match"? I'm asking because, for example, if I want to have two rules, one to match an IP and the other to match everything but that IP, I'd have to have two IPSets, one with the IP address and one with the IP non-match setting on.
Providing the cluster.fw file and vm_id.fw files down below for reference if needed
Code:
[OPTIONS]
policy_in: DROP
policy_out: ACCEPT
enable: 1
[ALIASES]
# SOME ALIASES HERE, TOO MANY TO INCLUDE
[IPSET local_ips]
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16
[IPSET not_local_ips]
!10.0.0.0/8
!172.16.0.0/12
!192.168.0.0/16
[RULES]
[group vm-to-net] # Do not allow inter-vlan comm
IN ACCEPT -source +dc/not_local_ips -log warning # Allow incoming from non-local IP addresses (internet)
OUT ACCEPT -source +dc/not_local_ips -log warning # Allow outgoing to non-local IPs (internet)
Code:
[OPTIONS]
enable: 1
ndp: 0
ipfilter: 1
policy_out: DROP
log_level_out: warning
dhcp: 0
log_level_in: warning
[RULES]
GROUP vm-to-netAlso, just referencing this, maybe it gets more views, as I find it quite important...
https://forum.proxmox.com/threads/pve-8-pve-firewall-status-no-such-alias.130202/#post-573149
Thanks in advance.
Last edited: