UPDATE: As a result of the research on this thread, it looks like like you cannot use private IPs behind your Proxmox host's true IP, and masquerade the traffic using NAT, as stated here
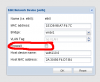
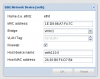
Using Proxmox 3.4, I've given my (Linux) guest both public and private network addresses.
How can I get the private addresses NAT-ed so that they can ping the public internet (they can ping each other, BTW)?
Here's my PVE config:
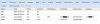
And on the host, I have:
on the guests:
Using Proxmox 3.4, I've given my (Linux) guest both public and private network addresses.
How can I get the private addresses NAT-ed so that they can ping the public internet (they can ping each other, BTW)?
Here's my PVE config:
And on the host, I have:
Code:
auto lo
iface lo inet loopback
iface eth0 inet manual
auto vmbr0
iface vmbr0 inet static
address 62.x.x.102
netmask 255.255.255.0
gateway 62.x.x.1
bridge_ports eth0
bridge_stp off
bridge_fd 0
auto vmbr1
iface vmbr1 inet static
address 10.10.10.1
netmask 255.255.255.0
bridge_ports none
bridge_stp off
bridge_fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '10.10.10.0/24' -o eth0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '10.10.10.0/24' -o eth0 -j MASQUERADEon the guests:
Code:
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet static
address 89.x.x.5
netmask 255.255.255.0
network 89.x.x.0
broadcast 89.x.x.255
gateway 89.x.x.1
# dns-* options are implemented by the resolvconf package, if installed
dns-nameservers 8.8.8.8
dns-search xxxxx
auto eth1
iface eth1 inet static
address 10.10.10.101
netmask 255.255.255.0
Last edited: