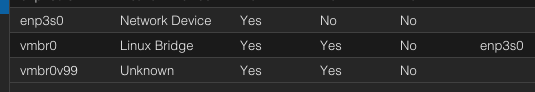
I have proxmox running on my mini ITX board and is doing just fine. It is running a number of roles including NAS, pfsense, homeassistant, etc and its barely working up a sweat. I measured the power consumption for the setup and found it be little higher than I would like so I looking for less power hungry alternatives.
I was wondering if I switch over from my current platform to a lowend NUC. Unfortuantely, it has a major limitation in that it only has single NIC. This NUC is quite lowend and does not support PCI passthrough so I am limited to using the bridges within proxmox.
I have setup pfsense previously using a single NIC on a standalone pc using VLAN and external smart switch and it was working fine.
It is possible to use a single NIC arrangement with proxmox and obtain net isolation using VLAN to seperate WLAN and LAN traffic.
I have the following throughts being to create a seperate bridge on VLAN 10 ( vmbr0.10) and link to the primary NIC. Then attach the pfsense WAN port the valn bridge. Also, attach the LAN to vmbr0.
Is this the best approach? Is there a better alternate solution?
If this is best approach, do I need to set up WAN port in pfsense to send the tagging (VLAN 10) or is tagging added and removed by the VLAN bridge. I have configured my switch to send all traffic tagged with VLAN 10 on the trunk port to port 8 of my switch which will be connected WAN. I will enforce proper tagging within the switch. All other ports are carrying untagged traffic for the LAN.
Is this secure enough for lab non commercial (home) environment? I know this is difficult question as secure enough is subjective. Lets just say, are there any serious security holes with this approach.
I have seen a few tutorials of people doing this, but they are all doing NIC passthrough which I presume is to enhance security (my equipment does not support PCI passthrough). I note, that I am not using passthrough on my current setup with my mini ITX, but using isolation between LAN and WAN by using seperate bridges connected to separate ports on the host.
I was wondering if I switch over from my current platform to a lowend NUC. Unfortuantely, it has a major limitation in that it only has single NIC. This NUC is quite lowend and does not support PCI passthrough so I am limited to using the bridges within proxmox.
I have setup pfsense previously using a single NIC on a standalone pc using VLAN and external smart switch and it was working fine.
It is possible to use a single NIC arrangement with proxmox and obtain net isolation using VLAN to seperate WLAN and LAN traffic.
I have the following throughts being to create a seperate bridge on VLAN 10 ( vmbr0.10) and link to the primary NIC. Then attach the pfsense WAN port the valn bridge. Also, attach the LAN to vmbr0.
Is this the best approach? Is there a better alternate solution?
If this is best approach, do I need to set up WAN port in pfsense to send the tagging (VLAN 10) or is tagging added and removed by the VLAN bridge. I have configured my switch to send all traffic tagged with VLAN 10 on the trunk port to port 8 of my switch which will be connected WAN. I will enforce proper tagging within the switch. All other ports are carrying untagged traffic for the LAN.
Is this secure enough for lab non commercial (home) environment? I know this is difficult question as secure enough is subjective. Lets just say, are there any serious security holes with this approach.
I have seen a few tutorials of people doing this, but they are all doing NIC passthrough which I presume is to enhance security (my equipment does not support PCI passthrough). I note, that I am not using passthrough on my current setup with my mini ITX, but using isolation between LAN and WAN by using seperate bridges connected to separate ports on the host.
Code:
PROXMOX
+-----------------------------------------+
| |
| +-----+ +-----+ |
| | VM1 | | VM2 | |
+-----+ | +--+--+ ++-----+ |
+-------+ | | | | | 192.168.1.3/24 |
| PC1 |--------+ SWITCH | +--+----++ +-------+ |
+-------| | | eth0 | | | | |
+-------| | 1+---------+ Vmbr0 +---+LAN | |
| PC2 |--------+ | || +--------+ | | |
+-------+ | | || | | | |
| | || +--------+ | | |
+----------------+8 | +--+ | | | |
Internet | | | | Vmbr0.0+---+WAN | |
+-----+ | +--------+ +-------+ |
| PFSENSE VM |
| |
+-----------------------------------------+
Last edited: