Hey Guys,
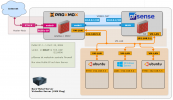
I try to build an environment with proxmox, hosted by kimsufi, with one external ip.
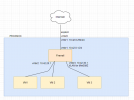
In this environment I installed a firewall and I want to get all traffic through the firewall.
Therefor I configured the following network interfaces:
I also tried it with the iptables like that:
The external ip is bound on the interface vmbr0.
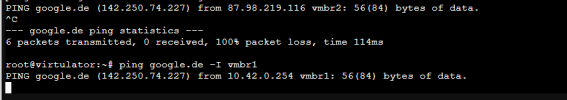
From the firewall iam able to ping the external interface, but nothing behind that. Neither can I reach my firewall or services behind it or next to it.
I appreciate every help if you guys need any further information, just ask!
if you guys need any further information, just ask!
I try to build an environment with proxmox, hosted by kimsufi, with one external ip.
In this environment I installed a firewall and I want to get all traffic through the firewall.
Therefor I configured the following network interfaces:
Bash:
auto lo
iface lo inet loopback
iface enp4s0 inet manual
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up echo 1 > /proc/sys/net/ipv4/conf/enp4s0/proxy_arp
iface enp5s0 inet manual
auto vmbr0
iface vmbr0 inet dhcp
bridge-ports enp4s0
bridge-stp off
bridge-fd 0
auto vmbr1
iface vmbr1 inet static
address 10.42.0.254/24
bridge-ports none
bridge-stp off
bridge-fd 0
post-up iptables -t nat -A POSTROUTING -s '10.42.0.0/24' -o vmbr0 -j MASQUERADE
post-up iptables -t nat -A PREROUTING -p tcp -d ex.te.rn.al --dport 443 -j DNAT --to-destination 10.42.0.1
post-up iptables -t nat -A PREROUTING -p tcp -d ex.te.rn.al --dport 4444 -j DNAT --to-destination 10.42.0.1
#external
auto vmbr2
iface vmbr2 inet static
address 10.42.20.254/24
bridge-ports none
bridge-stp off
bridge-fd 0
#internalI also tried it with the iptables like that:
Code:
post-up iptables -t nat -A POSTROUTING -s '10.42.0.0/24' -o vmbr0 -j MASQUERADE
post-up iptables -t nat -A PREROUTING -p tcp -d ex.te.rn.al -m multiport ! --dport 22,8006 -j DNAT --to-destination 10.42.0.1The external ip is bound on the interface vmbr0.
Code:
root@virtulator:~# iptables-save
# Generated by iptables-save v1.8.2 on Sun Dec 20 19:47:40 2020
*raw
:PREROUTING ACCEPT [65088:106935283]
:OUTPUT ACCEPT [43387:9004817]
COMMIT
# Completed on Sun Dec 20 19:47:40 2020
# Generated by iptables-save v1.8.2 on Sun Dec 20 19:47:40 2020
*filter
:INPUT ACCEPT [52437:104761064]
:FORWARD ACCEPT [5474:392261]
:OUTPUT ACCEPT [43438:9007605]
COMMIT
# Completed on Sun Dec 20 19:47:40 2020
# Generated by iptables-save v1.8.2 on Sun Dec 20 19:47:40 2020
*nat
:PREROUTING ACCEPT [7981:478653]
:INPUT ACCEPT [1505:70370]
:OUTPUT ACCEPT [106:6973]
:POSTROUTING ACCEPT [106:6973]
-A PREROUTING -d ex.te.rn.al/32 -p tcp -m tcp --dport 443 -j DNAT --to-destination 10.42.0.1
-A PREROUTING -d ex.te.rn.al/32 -p tcp -m tcp --dport 2222 -j DNAT --to-destination 10.42.0.10:22
-A POSTROUTING -s 10.42.0.0/24 -o vmbr0 -j MASQUERADE
COMMIT
# Completed on Sun Dec 20 19:47:40 2020
Code:
root@virtulator:~# pveversion
pve-manager/6.3-3/eee5f901 (running kernel: 5.4.78-2-pve)From the firewall iam able to ping the external interface, but nothing behind that. Neither can I reach my firewall or services behind it or next to it.
I appreciate every help