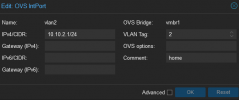
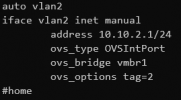
The title contains what I am trying to achieve.
My setup contains of a few virtual machines, most of them are in the same VLAN I have created for servers (I will refer to that as VLAN 100). One of my VM that hosts most of my services for home devices is in different VLAN (VLAN 2).
The setup works just fine and my firewall can route 1Gbe with relative ease. However I just feel it is a slight misuse of resources to route VM-VM traffic through firewall instead of routing the traffic inside Proxmox. Unfortunatelu I have not enough experience with Proxmox to know how to solve my problem. OVS seems to have Layer 3 capabilities, but I haven't found a noob-friendly guide on setting that up. Also I'm not actually sure if OVS is the go-to-solution for my problem.
TL;DR: What is the best way to achieve Layer 3 routing inside Proxmox for virtual machines inside different VLANs?
My setup contains of a few virtual machines, most of them are in the same VLAN I have created for servers (I will refer to that as VLAN 100). One of my VM that hosts most of my services for home devices is in different VLAN (VLAN 2).
The setup works just fine and my firewall can route 1Gbe with relative ease. However I just feel it is a slight misuse of resources to route VM-VM traffic through firewall instead of routing the traffic inside Proxmox. Unfortunatelu I have not enough experience with Proxmox to know how to solve my problem. OVS seems to have Layer 3 capabilities, but I haven't found a noob-friendly guide on setting that up. Also I'm not actually sure if OVS is the go-to-solution for my problem.
TL;DR: What is the best way to achieve Layer 3 routing inside Proxmox for virtual machines inside different VLANs?