Hello,
I have a proxmox installation with a vm inside that acts as a firewall. OPNSESE.
The traffic arriving from outside comes nat from vm-opnsense over the entire network.
For all the vm inside the hypervisor I have no problem, I can correctly nat any port.
If from the LAN I try to reach the proxmox hypervisor via ssh or web 8006, I can easily.
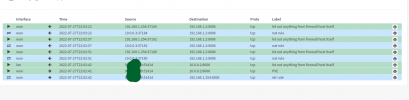
I can't get the 8006 from outside. I think I'm missing something about the proxmox network theory.
I tried disabling the proxmox firewall or adding a rule on the specific port but nothing.
What I did not understand ?
could anyone help me?
I have a proxmox installation with a vm inside that acts as a firewall. OPNSESE.
The traffic arriving from outside comes nat from vm-opnsense over the entire network.
For all the vm inside the hypervisor I have no problem, I can correctly nat any port.
If from the LAN I try to reach the proxmox hypervisor via ssh or web 8006, I can easily.
I can't get the 8006 from outside. I think I'm missing something about the proxmox network theory.
I tried disabling the proxmox firewall or adding a rule on the specific port but nothing.
What I did not understand ?
could anyone help me?